Mobile App Security: Best Practices and Strategies to Mitigate Risks
Smartphones and mobile applications are an essential part of our life. Mobile apps allow us to play games, book flights, socialize, and buy groceries. Recently mobile apps have made inroads into the banking and financial sector, where confidential details are exchanged. A security breach in the mobile application can lead to data theft, IP theft, unauthorized access, and fraud. That's why partnering with a trusted mobile app security provider is important. At Maruti Techlabs, as a leading product management consulting company, we specialize in mobile app security best practices and strategies to mitigate risks. Our team of experts can help your business avoid dissatisfied customers, revenue loss, and a tarnished brand image.
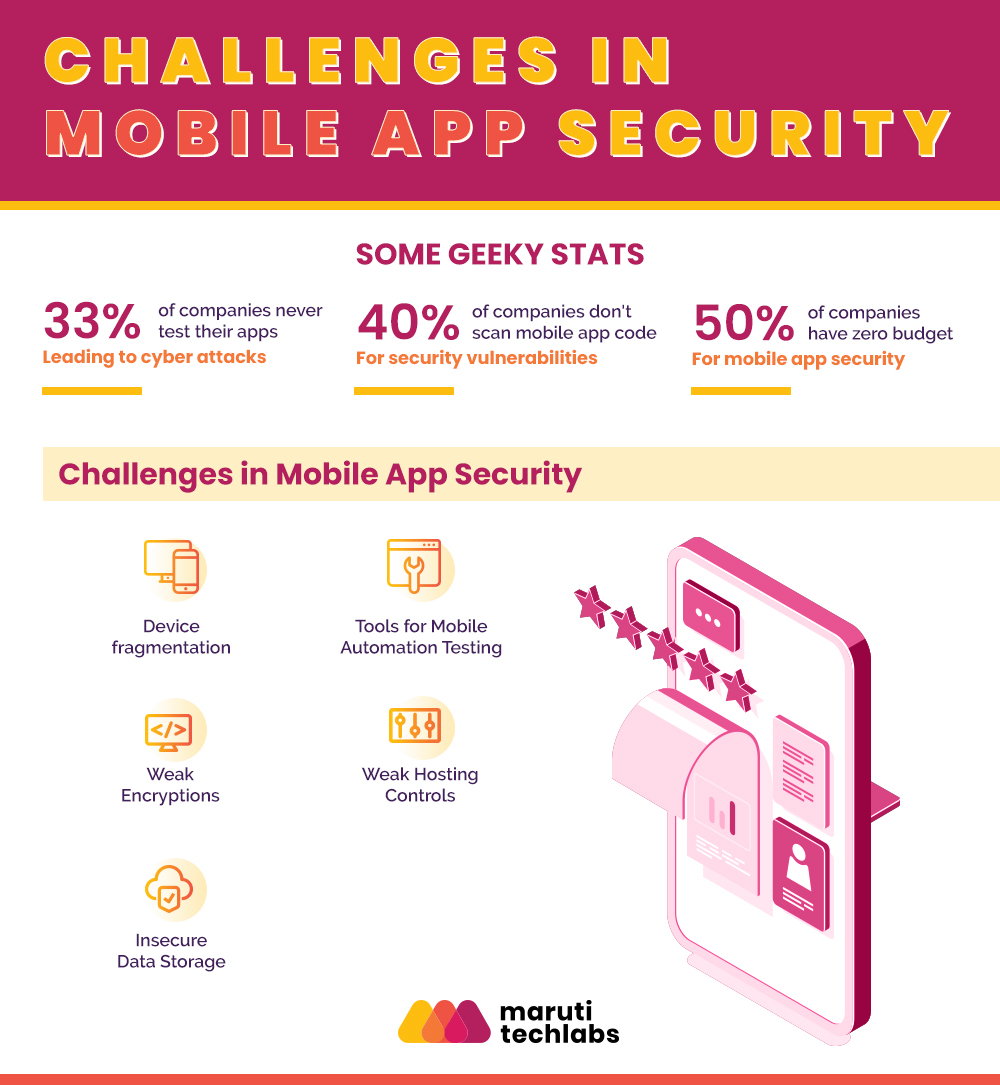
Challenges in Mobile App Security
1. Device Fragmentation
Mobile application testing needs to cover a multiplicity of mobile devices with different capabilities, features, and limitations. Identification of security vulnerabilities specific to devices makes performance testing a difficult task. The testing team can’t test release as fast as the development team is producing them, so they are becoming a bottleneck in the release process. This also leads to the production of low-quality apps. Most of the apps are made in iOS, Android or Windows environment. But there are different versions of each Operating System (OS) which have a different set of vulnerabilities. Testing of the app on each version is time-consuming and requires application tester to be aware of the loopholes.
Testing mobile app security across different devices is of paramount importance to protect user data, prevent unauthorized access, and safeguard the app from potential cyber threats. To ensure robust security for your mobile app, hire iOS app developers and Android developers from a company like ours to ensure robust security across devices.
2. Tools for Mobile Automation Testing
A reasonable approach to fragmentation requires the use of automation testing. But Traditional testing tools like Selenium or QuickTest Professional (QTP) weren’t designed with cross-platform in mind. So automation tools for mobile app and web application are different. While many test automation and testing tools for mobile have emerged, there is a dearth of full-fledged standard tools that can cater to every step of the security testing. The common mobile automation testing tools are Appium, Robotium, and Ranorex.
3. Weak Encryptions
A mobile app can accept data from all kinds of sources. In the absence of sufficient encryption, attackers could modify inputs such as cookies and environment variables. Attackers can bypass the security when decisions on authentication and authorization are made based on the values of these inputs. Recently hackers targeted Starbucks mobile users to siphon money out of their Starbucks mobile app. Starbucks confirmed that its app was storing usernames, email addresses, and passwords in clear text. This allowed anyone with access to the phone to see passwords and usernames just by connecting the phone to a PC.
4. Weak Hosting controls
When creating their first mobile applications, businesses often expose server-side systems that were previously inaccessible to outside networks. The servers on which your app is hosted should have security measures to prevent unauthorized users from accessing data. This includes your own servers, and the servers of any third-party systems your app may be accessing. It’s important for the back-end services to be secured against malicious attacks. Thus, all APIs should be verified and proper security methods should be employed ensuring access to authorized personnel only.
It applies even to a corresponding web app you create for your mobile application. For instance, if you choose ASP.NET as a framework to build your web app, hosting controls refer to controls provided by server administrators to manage different aspects of your web application. This is an essential feature and may require assistance from a Dot Net development company.
5. Insecure Data Storage
In most of the popular apps consumers simply enter their passwords once when activating the payment portion of the app and use it again and again to make unlimited purchases without having to re-input their password or username. In such cases, user data should be secure and usernames, email addresses, and passwords should be encrypted. For example, in 2012 a flaw in Skype data security allowed hackers to open the Skype app and dial arbitrary phone numbers using a simple link in the contents of an email. Design apps in such a way that critical information such as contact details, passwords, and credit card numbers do not reside directly on a device. If they do, they must be stored securely.
One of the best techs to choose concerning secure data storage is Python. Python is often used in conjunction with various databases, storage systems, and encryption libraries to enhance data security. The programming language offers a series of functionalities that add layers to your app's data security. The top features include:
1) Encryption
2) Hashing
3) Salting
4) Parameterized queries
5) Secure libraries
Upgrading your data security using the functionalities mentioned above may require the expertise of Python programmers. Investing in this can help your organization avoid data breaches, maintain user trust, and adhere to industry best practices."
Businesses should define standard secure practices during application development. Considering the following concerns, they can ensure security across every aspect of mobility operations:
- Data: How does the application fetch and display data?
- Network: How does the application access networks?
- Device: How vulnerable is the device to loss or theft?
- Application: How securely and effectively is the application coded?
Businesses should apply mobile strategy diligently make sure your mobile developers can think through unintended consequences of app design and security. Delivering an easy-to-use app will decrease the brand value if you put customer or enterprise data at risk.
To avoid redesigning and compromising user data, which adds more time for your app to reach the market while tarnishing your reputation, it's best to connect with a React.js web development company and security experts with experience in this field.
To address mobile app security challenges, partner with a top mobile app development company that prioritizes security in their development process and offers custom mobile application development services, including iOS and Android, with a strong focus on security. This helps ensure your app is protected against potential threats.
Building a secure mobile app is paramount. When selecting a partner for your SaaS development services, prioritize companies with a proven track record in robust user data protection and security best practices.
At Maruti Techlabs, we offer comprehensive product development services and solutions. Contact us for mobile app security concerns.




















