Cloud Security Services
Secure your cloud assets from costly breaches, data loss, and downtime with our multi-layered approach to cloud security services.
Cloud Security Services
Secure your cloud assets from costly breaches, data loss, and downtime with our multi-layered approach to cloud security services.
Unlock the Key to Secure Cloud Data With Our Cloud Security Services
As companies increasingly rely on cloud tech to power their operations, the associated risk continues to evolve. From data breaches to cyber-attacks, the threats to your cloud environment and the need for robust cloud security managed services, are constant.
At Maruti Techlabs, we understand the importance of protecting your cloud assets. Our multi-layered approach to cloud computing security services ensures advanced threat prevention for all your workloads across any environment. With our certified AWS and Azure experts, you can rest assured that your business is protected against costly breaches, data loss, and downtime.
Let us help you secure your cloud environment and safeguard your business from the constantly evolving digital age threats. Take advantage of our unrivaled incident expertise for ironclad cloud security solutions!
Cloud Security Assessment
Get a clear understanding of your cloud security risks with our cloud security assessment services. Our expert team conducts a comprehensive assessment of your cloud security footprint to identify potential vulnerabilities and provide a targeted strategy for remediation. Let us help you with a detailed analysis of your cloud security posture.
DevSecOps
Enhance the security of your applications by integrating robust security measures, safeguarding against cyber threats, optimizing development processes, and ensuring a secure user experience. Our team leverages state-of-the-art tools and technologies to provide end-to-end, secure cloud-based solutions for your modern-day applications.
Cloud Security Architecture
Design and implement a robust, secure architecture using our end-to-end cloud security architecture services. Our approach includes implementing security controls such as firewalls, intrusion detection, and prevention systems to protect against cyber threats and unauthorized access—partner with us to constantly protect all your cloud services and applications.
Disaster Recovery & Backup
Automate your disaster recovery and backup strategy with our cloud security services. We automate systems and data backups across regions to provide redundancy and availability for your business-critical applications and data. Our expert team develops and implements a comprehensive plan that ensures smooth operations in the face of disaster.
Cloud Security Consulting
Partner with our experienced cloud security consultants to identify risks and build a customized security strategy that aligns with your business objectives. Our consultants will collaborate with you to understand your unique security requirements and provide expert guidance to ensure your cloud infrastructure's security and adherence to compliance standards.
Penetration Testing
Test your entire cloud environment to find potential misconfigurations and vulnerabilities that could expose your infrastructure to attackers. Our expert team at Maruti Techlabs uses sophisticated tools and techniques to simulate real-world attacks. Our team also assists you in identifying potential security gaps and provides recommendations for remediation.
Data Encryption
Secure your sensitive data before moving it to the cloud by leveraging our data encryption services. We are masters at delivering a comprehensive data encryption solution that ensures data confidentiality, integrity, and availability. Our team creates a robust key management solution that allows only authorized access to the data, ensuring it is protected from unauthorized access.
Constant Monitoring of Servers
Ensure your cloud infrastructure's continuous security by constantly monitoring servers. Our team of Maruti Techlabs provides 24/7 monitoring and detection of any suspicious activity or data breaches. We use advanced tools and techniques to remediate any issues and ensure your servers remain secure immediately.
Data Loss Prevention
Build a robust system to protect against data loss caused by cyberattacks, misuse of authorized access, and accidental disclosure. Our consultant team at Maruti Techlabs uses sophisticated tools and techniques to monitor and prevent data loss scenarios. Our cloud-based managed security services assist you in creating comprehensive protection for your data in the cloud.
Constant Compliance Checks
Ensure compliance and governance across all public cloud environments with Maruti Techlabs cloud security compliance service. Our streamlined and automated compliance solutions help your organization meet industry and government regulations, auditing, and reporting. Stay ahead of regulatory compliance with our expert team of cloud security professionals.
Boundary protection layer
The first layer of defense for cloud security consists of border routers, firewalls, intrusion protection systems, demilitarized zones, wireless security, and external gateways. Each of them has specific functionality. For example, border routers are responsible for stopping unauthorized access, firewalls control traffic based on rules, and wireless security ensures secure access.
Service Protection Layer
Service protection uses Public Key Infrastructure (PKI) or cryptographic keys for secure and authenticated data exchange. Access lists control the data packets that go through router interfaces. Furthermore, Intrusion Detection and Prevention Systems (IDPS) monitor network traffic, identify suspicious activities, and protect against Distributed Denial of Service (DDoS) attacks.
Data Protection Layer
Data protection includes backup and recovery services to restore data in case of loss or corruption. The data protection layer is critical in cloud security services. It involves using Host Intrusion Detection Systems (HIDS) to detect suspicious activity on the network. HIDS are also useful in detecting attacks from within the system. Antivirus solutions are employed to safeguard data from malicious activity such as viruses, worms, and other malware.
Boundary protection layer
The first layer of defense for cloud security consists of border routers, firewalls, intrusion protection systems, demilitarized zones, wireless security, and external gateways. Each of them has specific functionality. For example, border routers are responsible for stopping unauthorized access, firewalls control traffic based on rules, and wireless security ensures secure access.
Service Protection Layer
Service protection uses Public Key Infrastructure (PKI) or cryptographic keys for secure and authenticated data exchange. Access lists control the data packets that go through router interfaces. Furthermore, Intrusion Detection and Prevention Systems (IDPS) monitor network traffic, identify suspicious activities, and protect against Distributed Denial of Service (DDoS) attacks.
Data Protection Layer
Data protection includes backup and recovery services to restore data in case of loss or corruption. The data protection layer is critical in cloud security services. It involves using Host Intrusion Detection Systems (HIDS) to detect suspicious activity on the network. HIDS are also useful in detecting attacks from within the system. Antivirus solutions are employed to safeguard data from malicious activity such as viruses, worms, and other malware.
Teams We Offer
Ideation to MVP Team
The ideation to MVP team launches your idea into the market. It helps you validate your idea and gather feedback before going all-in with full-scale development. Our team leverages low-code / no-code technologies to build quickly, iterate, and ship a minimum viable version of your product.
The ideation to MVP team helps you verify your business hypothesis, validate the products functionality, reach product-market fit, and map out the product roadmap accordingly.
Scale & Maturity Team
After achieving product-market fit, our scale and maturity team focuses on customizing the product. The product development team performs product testing, analyzes the results, draws conclusions, and applies them to scaling the product. They guarantee incremental and iterative delivery and improvement.
The North Star for this team is assisting you in developing an internal culture centered around data-driven product decisions and designing products for stability and scalability.
Support & Care Team
This team closely monitors the application's customer service, experience, data integrity, & smooth running. Two weeks after the development of the product is concluded, the support & hypercare team takes over, & the core product team disintegrates.
During these two weeks, knowledge transfer sessions are held between the product team and the support team. They ensure intensive support and maintenance of the product. The maintenance activities are carried out based on an SLA-based approach.
Experience next-level cloud security services.
Our Development Process
We follow Agile, Lean, & DevOps best practices to create a superior prototype that brings your users’ ideas to fruition through collaboration & rapid execution. Our top priority is quick reaction time & accessibility.
We really want to be your extended team, so apart from the regular meetings, you can be sure that each of our team members is one phone call, email, or message away.
Client Segment
Startup / SME
Build from scratch, improve what you have, or do something entirely different— we’ve got you covered.
- Build Something New
Map out your idea, determine what to build, and collaborate to bring an MVP or a solid 1.0 to life. - Improve What You Have
Build a new version of your existing app or add new features to your system with our expertise. - Discover What You Need
Not sure where to start? We also offer code and architecture reviews, strategic planning, team training, and more.
Enterprise
We deploy our best-in-class assets to help you build, innovate, and accelerate your business.
- Seamless Integration
We blend into your team, leading the project forward with solid communication and expertise. - Leadership & Management
Our management excels at managing remote teams and complex projects and providing technical guidance. - Transparency & Agile
We leverage tools like Trello, Skype, JIRA, and Slack to achieve transparency, synergy, and better project visibility.
Native Security Automation
Native security automation ensures consistency in configuration management and Infrastructure-as-Code (IaC) scripts and enhances server and Kubernetes hardening practices.
Secure Posture Identification
Leveraging secure posture identification, one can monitor security policies and configurations, perform vulnerability analysis, identify risks, and assess the effectiveness of security controls.
Cloud Security Observability
Security observability plays a vital role in ensuring the security of modern event-driven serverless applications. Integrated security policies and observability are necessary to ensure the management and analysis of security events.
Time & Material Model
Enjoy complete control of the development progress, pace, & cost of the project. We recommend the time & material engagement model for dynamic business requirements. In this model, the project cost is measured in execution time and resources deployed.
- Flexibility
- Easy Control
- Transparency
Offshore Dedicated Team (ODT) Model
We put dedication into the Offshore Dedicated Team (ODT). Our ODT model involves a team of skilled developers, testers, and managers working diligently on your project. With Maruti Techlabs, you benefit from a wide range of skills, expertise, and resources.
- Great for Large Projects
- Efficiency
- Adaptability
Team Extension Model
Add skills & bandwidth to your team by hiring additional developers on-demand. Our developers seamlessly integrate into your existing team. With on-demand team extension, you can fulfill your skill-specific requirements & scale the team at your pace.
- Faster Time-to-Market
- Focus
- Scalability
Time & Material Model
Enjoy complete control of the development progress, pace, & cost of the project. We recommend the time & material engagement model for dynamic business requirements. In this model, the project cost is measured in execution time and resources deployed.
- Flexibility
- Easy Control
- Transparency
Offshore Dedicated Team (ODT) Model
We put dedication into the Offshore Dedicated Team (ODT). Our ODT model involves a team of skilled developers, testers, and managers working diligently on your project. With Maruti Techlabs, you benefit from a wide range of skills, expertise, and resources.
- Great for Large Projects
- Efficiency
- Adaptability
Team Extension Model
Add skills & bandwidth to your team by hiring additional developers on-demand. Our developers seamlessly integrate into your existing team. With on-demand team extension, you can fulfill your skill-specific requirements & scale the team at your pace.
- Faster Time-to-Market
- Focus
- Scalability
Technology Stack
14+ years experience
Start as quickly as a week
Recurring cost of training & benefits - $0
Risk of failure? Next to none. 4.8/5 NPS on Clutch
Certified PMs & delivery teams
Rapid deployment & on-time delivery of projects
Complete transparency
Robust communication across shared channels
Agile & lean startup methodology
Experience across 16 industries
We take data protection seriously. Way too seriously!



Awards & Recognitions
We’re proud to accept industry accolades for our commitment to unparalleled results, client service and continuous growth.
Our People = Our Strength
We are as good as our team. And that's why we believe in hiring, training, and retaining the best talent. From following a robust hiring process to ensuring the best project deployment tools, our practices and frameworks reflect our aim to provide the best services and be the best software development team in the market.
We take pride in the broad spectrum of world-class products built by our team. Our team of over a hundred software developers is well-versed in different combinations of JavaScript, React Native, Python, Java, Scala, PHP, and other languages. Our team's areas of expertise also include many underlying platforms, APIs, IEDs, databases, and frameworks.
Project Managers
Technical Architects
Data Scientists
Business Analysts
Software Engineers
Integration & Release Engineers
QA Engineers
System Designers
DevOps Engineers
UI/UX Designers
IT Personnel
Support Personnel
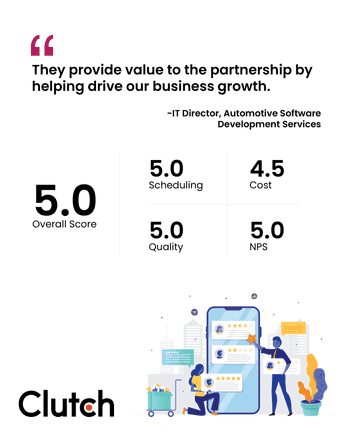
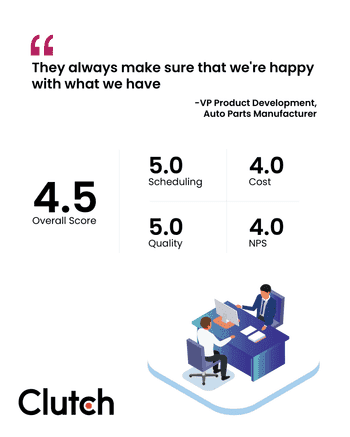
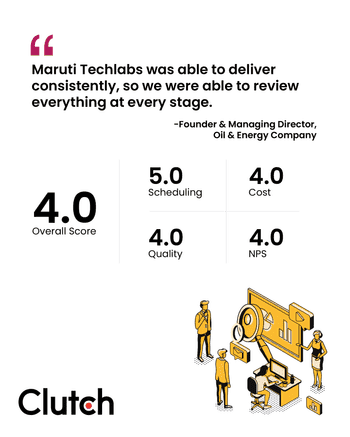
More social proof incase you're still on the fence
Looking For Other Services?
FAQs
Cloud security as a service encompasses a range of services designed to reduce risk and enhance compliance within cloud environments. Given the intricate nature of these environments, a one-size-fits-all solution cannot adequately safeguard them. However, cloud-based security services managed by third-party entities offer several advantages:
- Experts with the requisite knowledge can monitor, detect, and respond to threats effectively, ensuring thorough and appropriate mitigation.
- Managed cloud security service providers are typically trained to assist organizations in achieving regulatory compliance, which often falls beyond an organization's expertise.
- By offloading cyber incident handling to external specialists, your IT staff can dedicate their efforts to supporting your core business operations.
Some of the most common types of cloud security services are -
- Data Loss Prevention: With the vast amount of data in the cloud, DLP services detect and prevent unauthorized access to sensitive information, effectively protecting against data breaches and loss.
- Identity and Access Management: IAM services ensure that users have appropriate access privileges, restricting them to actions and resources relevant to their roles. This minimizes the risk of unauthorized access and misuse of cloud resources.
- Intrusion Detection: Intrusion detection solutions monitor network traffic for suspicious activities and potential threats, preventing threat actors from gaining a foothold in the system and exploiting vulnerabilities.
- Security Information and Event Management (SIEM): SIEM solutions collect and analyze log and event data from multiple security tools, generating alerts based on predefined rules. This enables threat detection and incident response teams to respond to security threats quickly.
- Encryption: Encryption ensures the confidentiality of data by making it unreadable to unauthorized individuals. It is a fundamental requirement for compliance with data privacy regulations, protecting sensitive information stored in the cloud.
Cloud security is essential for the following reasons:
- Enhanced Data Security: Cloud security safeguards data with encryption, access controls, and backup/recovery measures. Advanced features like multi-factor authentication and intrusion detection add extra protection.
- Improved Business Continuity: Robust backup, recovery, and failover capabilities ensure seamless operations during disasters or outages. Quick recovery minimizes disruptions.
- Scalability and Flexibility: Cloud security adapts to changing needs, scaling up or down as required. Organizations can choose tailored security measures.
- Cost-effectiveness: Cloud security eliminates upfront investments and reduces maintenance costs. Pay-as-you-go models provide cost control.
- Compliance: With certifications and audits, cloud security helps meet data protection regulations.Access controls and encryption aid compliance efforts.
Integrating diverse cloud security services into a cohesive defense system can be challenging, but following these valuable guidelines can maximize their effectiveness.
- Understand shared security responsibility: Know your role and the responsibilities of your cloud provider in the shared security model.
- Clarify security measures: Evaluate and understand the security controls, disaster recovery plan, regulatory compliance, access controls, encryption methods, and technical support provided by your cloud provider.
- Utilize IAM solution: Minimize misconfigurations by implementing an Identity and Access Management solution to control user access and limit administrative privileges.
- Implement an automated defense strategy: Create an integrated and automated defense strategy with multiple security layers to enhance threat detection, response, and redundancy.
- Consider outsourcing security: If lacking in-house cybersecurity resources, consider outsourcing cloud security services to Managed Security Service Providers (MSSPs) for expert management, additional services, and efficient threat monitoring and response.
Key components in cloud security work together to establish a comprehensive and robust security framework for cloud environments.
- Identity and Access Management (IAM): Controls access to cloud resources with features like SSO, MFA, and RBAC.
- Data Encryption: Protects stored data by converting it into an unreadable format using encryption algorithms.
- Firewall: Safeguards cloud resources by monitoring and controlling network traffic based on security rules.
- Intrusion Detection and Prevention (IDP): Identifies and prevents attacks by analyzing network traffic and system logs.
- Vulnerability Management: Identifies and addresses vulnerabilities through regular scanning and patching.
- Virtual Private Network (VPN): Establishes a secure, encrypted connection for remote access to cloud resources.
Migrating to or operating in the cloud requires careful consideration of security measures to protect your data and infrastructure. Here’s what you must ask when migrating to or operating in the cloud.
- What security certifications and compliance standards does the cloud service provider adhere to?
- What physical security measures are in place at the cloud provider's data centers?
- What incident response and disaster recovery plans are in place?
- How are user access and authentication managed?
- What network security measures are implemented?
- How is data segregation achieved in a multi-tenant environment?
- What are the backup and data retention policies?
- How are security updates and patches managed?
- Is there visibility and transparency into security controls and events?
Many companies misunderstand that transferring their infrastructure to the cloud can be achieved effortlessly. However, the reality is that shifting from on-premises infrastructure to the cloud requires careful attention to security.
The cloud operates distinctly from traditional IT environments, necessitating a dedicated focus on unique security considerations. Whether you're embarking on cloud migration, operating in a hybrid environment, or adopting a cloud-first approach, implementing cloud security strategy services is essential to mitigate risks effectively.
In today's rapidly evolving digital landscape, harnessing the potential of cloud infrastructure while ensuring robust security measures is vital for businesses to thrive. With our unrivaled cloud security expertise and dedication to protecting your valuable assets, we provide compelling reasons why partnering with us is the smart choice for your cloud security needs.
- Unmatched Expertise: Our seasoned experts possess deep cloud security knowledge, ensuring constant infrastructure protection.
- Tailored Solutions: We customize our services to meet your unique security requirements, providing comprehensive risk assessments and robust security architectures.
- Cutting-edge Technology: Leveraging advanced tools and technologies, such as AI-based threat detection and encryption mechanisms, we fortify your cloud against evolving threats.
- Proactive Monitoring: We detect and mitigate security breaches through vigilant surveillance and rapid incident response, minimizing downtime and safeguarding your data.
- Seamless: Whether migrating or expanding your cloud presence, our cloud services and security seamlessly integrate with leading platforms like AWS, Azure, and Google Cloud, ensuring a smooth transition with enhanced security.