

Why Identity Server is the Go-To Solution for User Management






The engineers would be aware of how difficult it is to manage and regulate user and access management in SaaS applications. Defining user roles and permissions based on their accessibility, subscriptions, and organizational structure can essentially affect your product scalability and experience if not done correctly.
Hey there! This blog is almost about 1500+ words long & not everyone likes to read that much. We understand that.
This is precisely why we made a podcast on the topic. Hamir Nandaniya, VP of Engineering at Maruti Techlabs, talks to Bikshita Bhattacharyya about using an Identity Server to centralize your application’s access management & user authentication.
He also talks about what his client was using before Identity Server & the need to switch to an identity server. The talk also focuses on the challenges faced during the implementation, its working, benefits, and more! Here is a small snippet from that episode. Check it out!
An efficient means of user management is through centralized authorization. And that is where IdentityServer comes into the picture. IdentityServer is an authentication server designed to provide a common way to authenticate requests to all of your applications, regardless of whether they’re web, native, mobile, or API endpoints.
Identity Server acts as a central database that stores user’s credentials. The identity server is checked to authenticate user access as it is a core part of any identity and access control infrastructure. In a nutshell, an identity server is a piece of software that issues security tokens to clients.
Numerous routine informational transactions occur every day in the IT outsourcing industry. These include yet are not restricted to online invoices, product catalogue, new recruitment information, salary details, etc. For each of these informational transactions, the company must determine who is allowed to view its data. Information relating to accounting and human resources must be restricted to employee use only.
Usually, applications need to support the following scenarios:
Typically, every layer of the physical infrastructure(front-end, middle-tier, and back-end) protects identity data and APIs. Furthermore, it has to implement authentication and user authorization – often against the same user store.
Outsourcing these fundamental security functions to an identity provider prevents copying that functionality across those applications and endpoints.
Security concerns are divided into two parts :
Authentication is necessary when an application needs to know the identification of the current user. Typically these applications handle data on behalf of that user. They need to make sure that this user can only access the data for which he/she is permitted. The most common example of that is (classic) web applications.
The most well-known authentication protocols are SAML2p, WS-Federation and OpenID Connect – SAML2p being the most famous and the most widely used.
OpenID Connect is the latest of the three protocols however is viewed as the future since it has the maximum potential for contemporary applications. It was designed for mobile application scenarios right from the start and is created to be API-friendly.
Applications have two primary approaches to communicate with APIs – using the application identity, or allocating the user’s identity.
OAuth2 is a convention that permits applications to request access tokens from a security token service and utilize them to communicate with APIs. This delegation reduces intricacy in both the client applications and the APIs since confirmation and approval can be at the centre stage.
OpenID Connect and OAuth 2.0
OpenID Connect and OAuth 2.0 are very alike – in fact, OpenID Connect is an extension of OAuth 2.0. The two primary security challenges, API access and authentication, are wrapped into a single protocol. This protocol often takes a single round trip to the security token service.
The association of OpenID Connect and OAuth 2.0 is the best approach to secure modern applications for years to come. IdentityServer4 is an implementation of these two conventions and is highly optimized to tackle the run of the mill security issues of today’s mobile, native and web applications.
Managing user identity can be a challenging, but with our custom web application development services, we can integrate an identity server to simplify the process. Our team of experts can guide you through the common web app scenarios and security concerns to ensure seamless user management.
Many organizations permit access to information on a per-application footing. For example, an employee may be required to set up a username and password to access the company’s health benefits and a separate username and password to access the HR department’s online forms.
An administrator deciphers the organization’s user’s input into a data format that the service can perceive for each website or service. Each service added to the company must be planned and maintained independently.
A company has to store and access multiple types of information through its enterprise. Similarly, various enterprise users must use that information to run smoothly for the company’s business. This is where Identity Server and identity service provider come to the rescue.
Identity Server reduces managerial costs and eliminates the unnecessary user information associated with per-application solutions. Identity Server creates a sole record entry for every enterprise user.
It allows an administrator to assign specific rules or approaches overseeing which information or services each user can access. Identity Server enables a user to access multiple resources within the organization significant with just one single identity.
Identity Server can be utilized to verify actual users through sign-in forms and service-based verification. The latter typically involves token issuance, validation, and renewal without any UI. IdentityServer is designed to be an adaptable solution. Each case is mainly customized to suit an individual organization and set of applications’ needs.
When a company user or an external application tries to access information stored on a company’s web server, the API gateway intercepts the request and directs it to Identity Server. Identity Server asks for the user credentials – a username and password.
If the credentials match those stored in the central Directory Server, the Identity Server validates that the user is who he claims to be. Furthermore, the Server assesses the rules in line with the user’s identity. It then determines whether the user is allowed to view the requested information or not.
At last, the Identity Server either grants or denies the user access to the information.
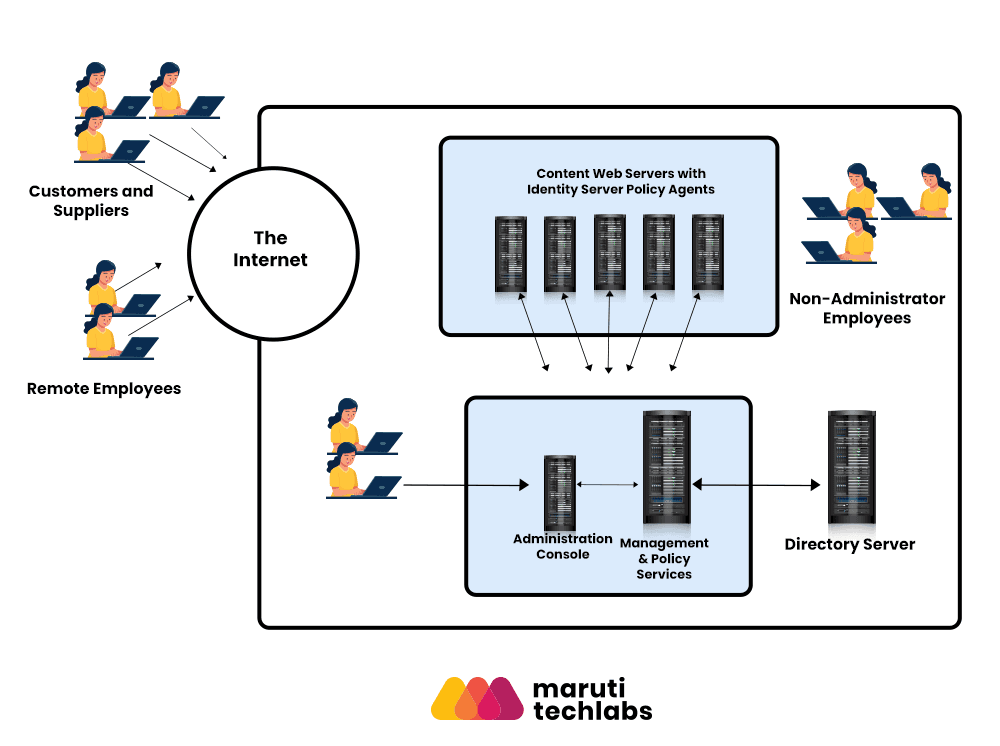
The image above illustrates how Identity Server intercepts requests from users before allowing or denying access.
Identity Server combines four significant features into a single product that can be viewed in a single administration console:
1. Identity Administration
Identity Server provides an identity structure for creating and overseeing directory objects such as organizations, groups, roles, and user IDs.
2. Access Management
Access management feature makes it possible to verify whether a user is who he says he is. The user is authorized to access application servers used within the organization.
3. Service Management
Identity Server provides a service management SDK that developers can use to register and unregister services. It also helps to manage schema and configuration information.
4. Federation Management
Identity federation allows an individual to log in at one service provider’s site and move to an affiliated service provider site without re-authenticating or re-establishing organizations.
Do you wonder how Identity Server addressed our client’s user management woes? Hamir Nandaniya does a deep dive on how adopting Identity Server and Access Management can benefit your organization and clients with improved user experience, regulatory compliances, and security issues.. Take a look at the video below 👇
There are many benefits of using an Identity server, especially when anyone has a suite of products like GSuite and wants to implement authentication and authorization in API(s) out of the box.
Other benefits include increased business agility, organization management, regulatory compliance and security best practices.
For businesses seeking to streamline their app development services while ensuring robust user management and security, implementing an identity server is a smart choice.
Did you find the video snippet on how we overcame the challenges of implementing Identity Server for our client to be insightful? We have a ~21 min video where Hamir Nandaniya gets into the weeds, and we discuss about using Identity Server to centralize your application’s access management and user authentication. Take a look –
By now, you must have gained an in-depth understanding of what an identity server is, how it works, its importance, as well as the security concerns it helps nullify. At Maruti Techlabs, we have worked with clients worldwide to solve different identity management requirements. We can help you build excellent Identity and Access Management (IAM) solutions that provide enhanced, seamless and secure digital experiences for your clients and speed digital transformation efforts.
Modernizing an enterprise application can significantly enhance its overall performance. As a technology solutions leader, Maruti Techlabs can help you modernize your IT environment. Our application modernization services deliver strategic and tactical, leveraging advancements and innovation to deliver relevant business transformation solutions.
Our team of product engineers bring to the table a great deal of experience and technical prowess. If you're looking for custom web app development services in Dallas, get in touch with us today to start your journey of digital transformation.
Identity Server is an open-source framework that provides authentication, authorization, and single sign-on (SSO) capabilities for modern applications and APIs.
It centralizes authentication, supports multiple identity providers, improves security, and simplifies user access control across distributed applications.
Yes. Identity Server supports SSO across web, mobile, and API-based applications, enabling a seamless and secure user experience.
Absolutely. Identity Server includes features like OAuth2, OpenID Connect, role-based access control, multi-factor authentication, and API security—making it ideal for large-scale systems.
Yes. It integrates easily with Google, Azure AD, Microsoft, Facebook, Okta, and other third-party identity providers.
Yes. It follows modern security standards, supports token-based authentication, and reduces the risk of unauthorized access through centralized identity management.


