

The Basics of DevSecOps: Building Security into DevOps Culture






As businesses embrace faster software delivery cycles to remain competitive, DevOps security has emerged as the preferred approach for rapid development and operations collaboration. However, the increasing pace of development often leaves traditional security methods struggling to keep up, leading to potential vulnerabilities. This is where DevSecOps steps in—a model that integrates security seamlessly throughout the software development lifecycle (SDLC).
DevSecOps removes these silos, bringing together developers, operations staff, and security team members at each phase.
This article delves into the new and refined methods of DevSecOps implementation and breaks down some obstacles to DevOps security.
As digital landscapes evolve, traditional methods like manual code reviews, periodic security audits, and perimeter defenses can’t keep pace with the demands for robust, continuous security.
DevSecOps emerges as a solution to these challenges, integrating security directly into the DevOps workflow, ensuring security isn’t an afterthought but an integral part of the entire development cycle.
Incorporating DevSecOps isn’t just about security; it’s about building resilience and trust within fast-moving development cycles.
Key Industry Statistics
These stats underline the growing need for DevSecOps, as traditional security approaches are no longer sufficient in today’s fast-paced development environments.
So, how can businesses start adopting DevSecOps to address these crucial needs? Let’s explore the specifics in detail.
Transitioning to a DevSecOps model ensures that security is an integrated part of the development process, fostering a more proactive approach to identifying and resolving security issues.
The objective of DevSecOps is cross-functional collaboration involving the development and operations teams. The concept is that security should be directly integrated into the SDLC instead of having a separate phase. This avoids security as a relic of afterthought and catches vulnerabilities much earlier.
Before exploring how DevSecOps reshapes security practices, it's helpful to compare it to traditional methods to understand why this model is gaining traction. While old practices cause a delay due to security, DevSecOps is flexible and provides an integrated solution.
Comparison: Traditional Approach vs. DevSecOps Approach
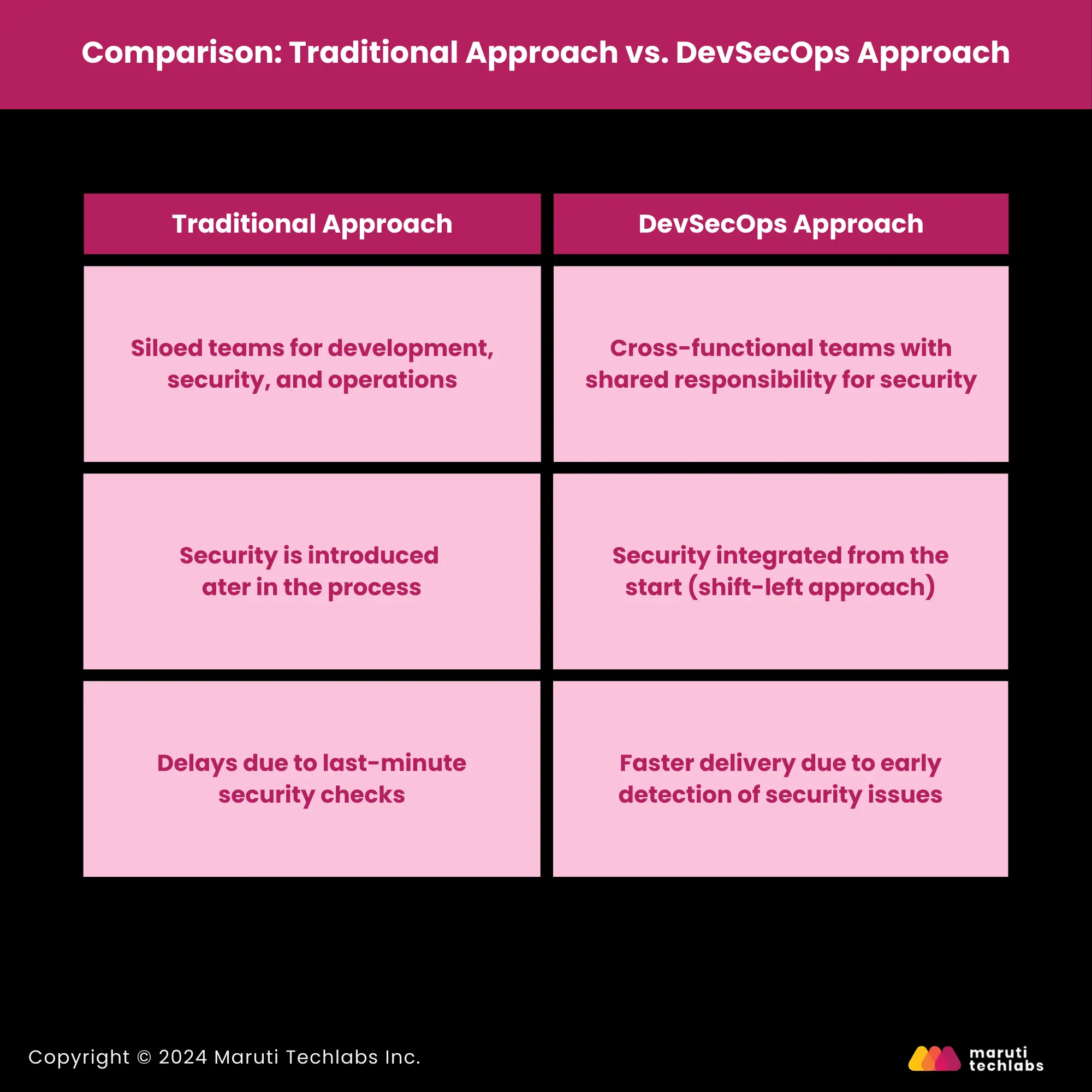
Traditional Approach | DevSecOps Approach |
| Siloed teams for development, security, and operations | Cross-functional teams with shared responsibility for security |
| Security is introduced later in the process | Security integrated from the start (shift-left approach) |
| Delays due to last-minute security checks | Faster delivery due to early detection of security issues |
The “shift-left” strategy encourages security teams to actively participate in planning and designing the software, reducing delays during final code reviews.
A shared responsibility model is critical for DevSecOps' success. In this model, security becomes part of the development and operations teams' objectives. Everyone is accountable for ensuring that security practices are followed throughout the pipeline.
This approach cultivates a culture where security is not limited to one team but is embedded throughout every phase of the development process, resulting in more secure and resilient software.
Integrating security into every development phase requires a shift in mindset and approach. Educating and collaborative efforts between security and development teams are essential to nurturing a secure environment.
One of the challenges in traditional security approaches is the disconnect between developers and security experts. Organizations can close this gap by educating and training development teams on secure coding practices.
Collaborative security reviews, code audits, and hands-on workshops between the development and security teams promote a culture of mutual learning and help identify potential security flaws early in the cycle.
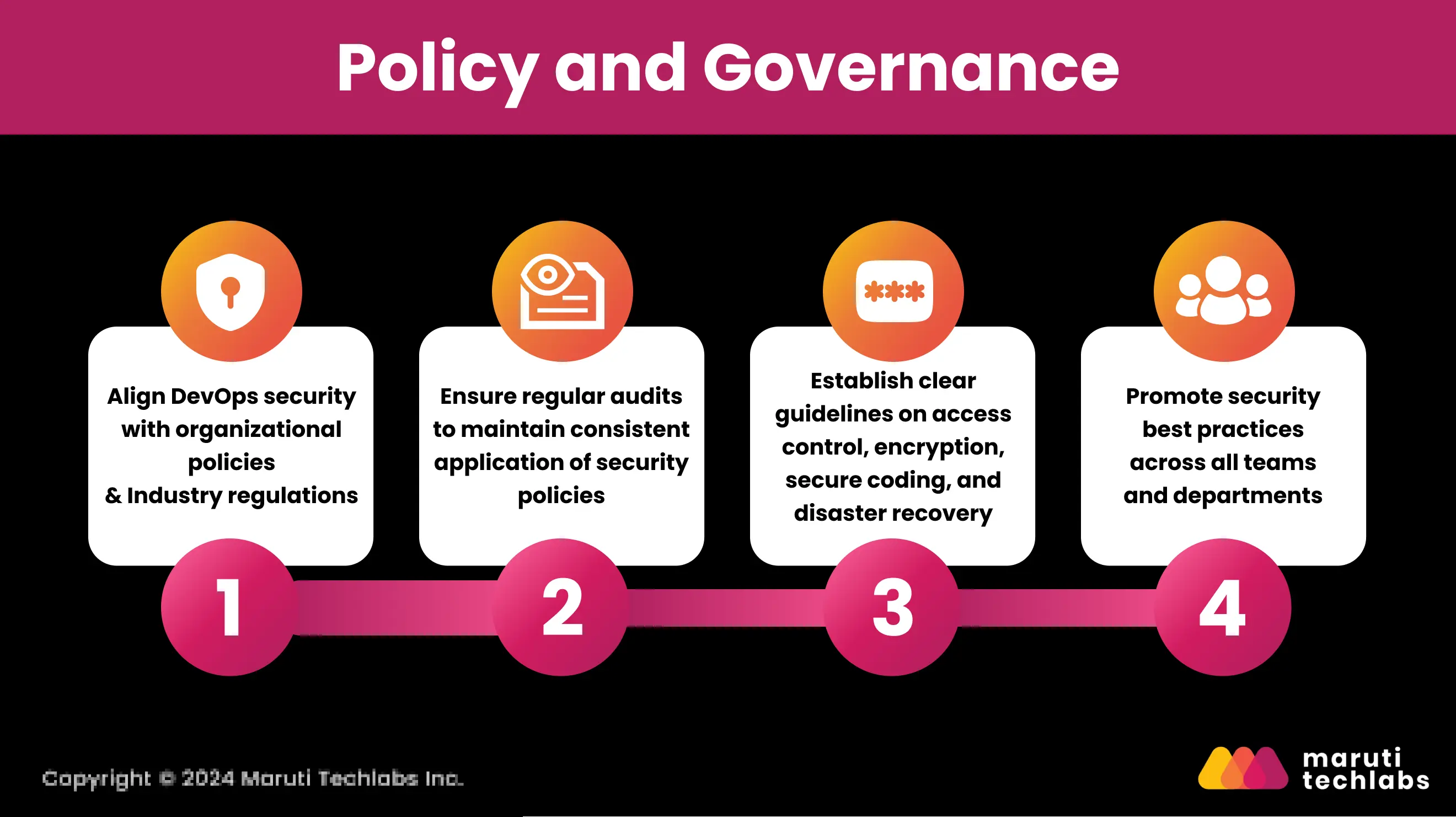
Aligning DevOps security with organizational policies creates a cohesive framework for ensuring compliance with industry regulations and promoting security best practices across all teams and departments.
DevOps security practices should align with the company’s overall security policies, including data protection regulations like GDPR or HIPAA. For instance, if your organization handles sensitive customer data, you’ll need to ensure that security protocols meet the standards set forth by these regulations.
The governance framework should include regular audits to ensure teams consistently apply security policies across the development and operations landscape.
To ensure the policies do not break through industry regulations and best practices, the DevOps processes provide clear security policies that ensure standard access control, encryption, secure coding, and disaster recovery procedures.
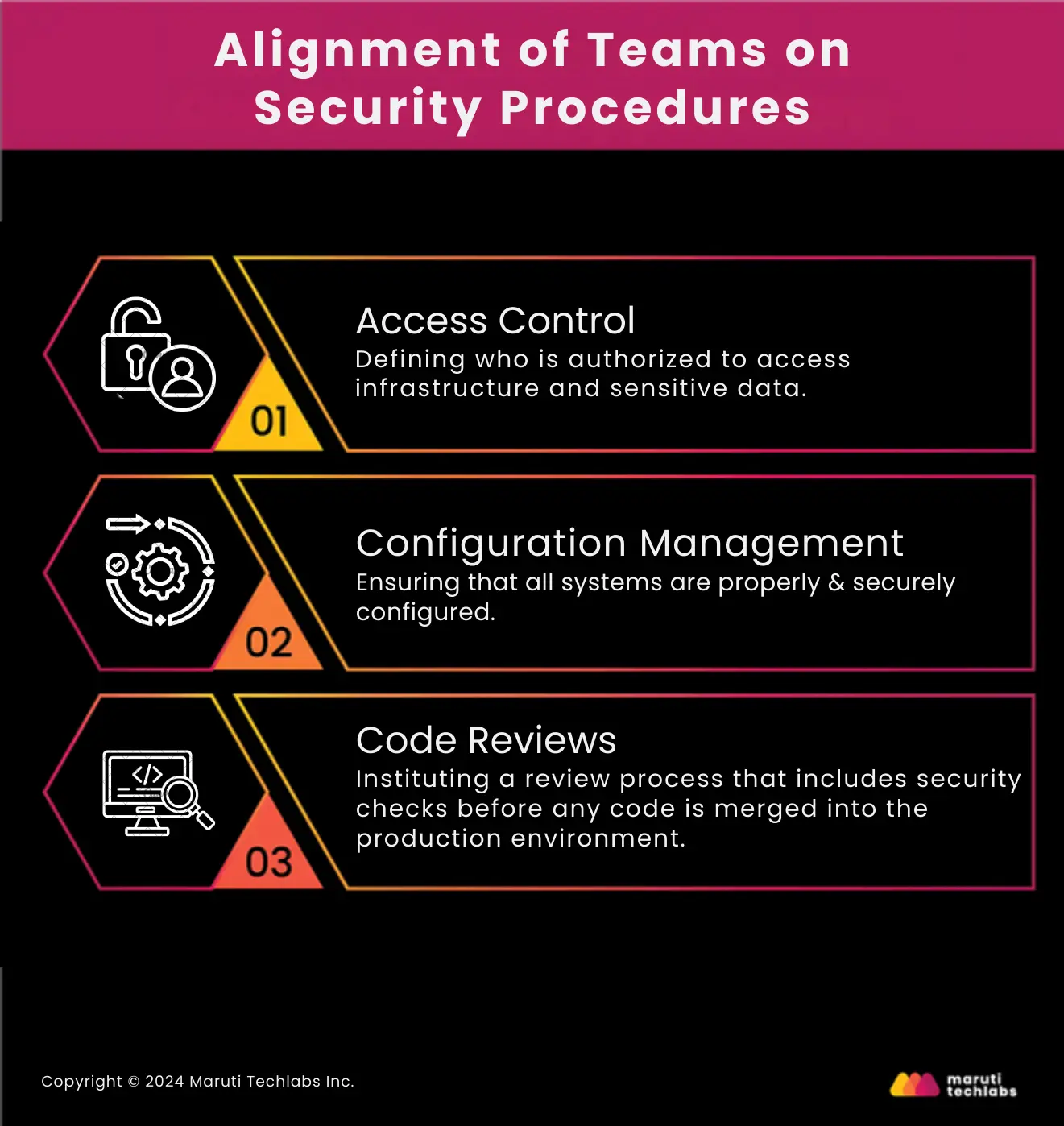
Security governance ensures that all teams are aligned on critical security procedures:
Automation in security processes can make a difference in further streamlining security.
Automating security processes allows organizations to scale their security practices while maintaining the agility needed to compete in today's digital landscape. It ensures consistent and reliable security checks with minimal manual intervention.
With the rise of cloud-native architectures, microservices, and containerized environments, the complexity of modern software systems has surged. This complexity introduces many potential vulnerabilities at every layer of the development stack.
These have made managing dependencies, securing APIs, and complying with distributed systems much tougher. Manual security checks are sufficient, time-consuming, and far from capable of identifying all threats. Human errors, along with the sheer scale of code and infrastructure changes, also increase the risks tied to vulnerabilities sneaking through.
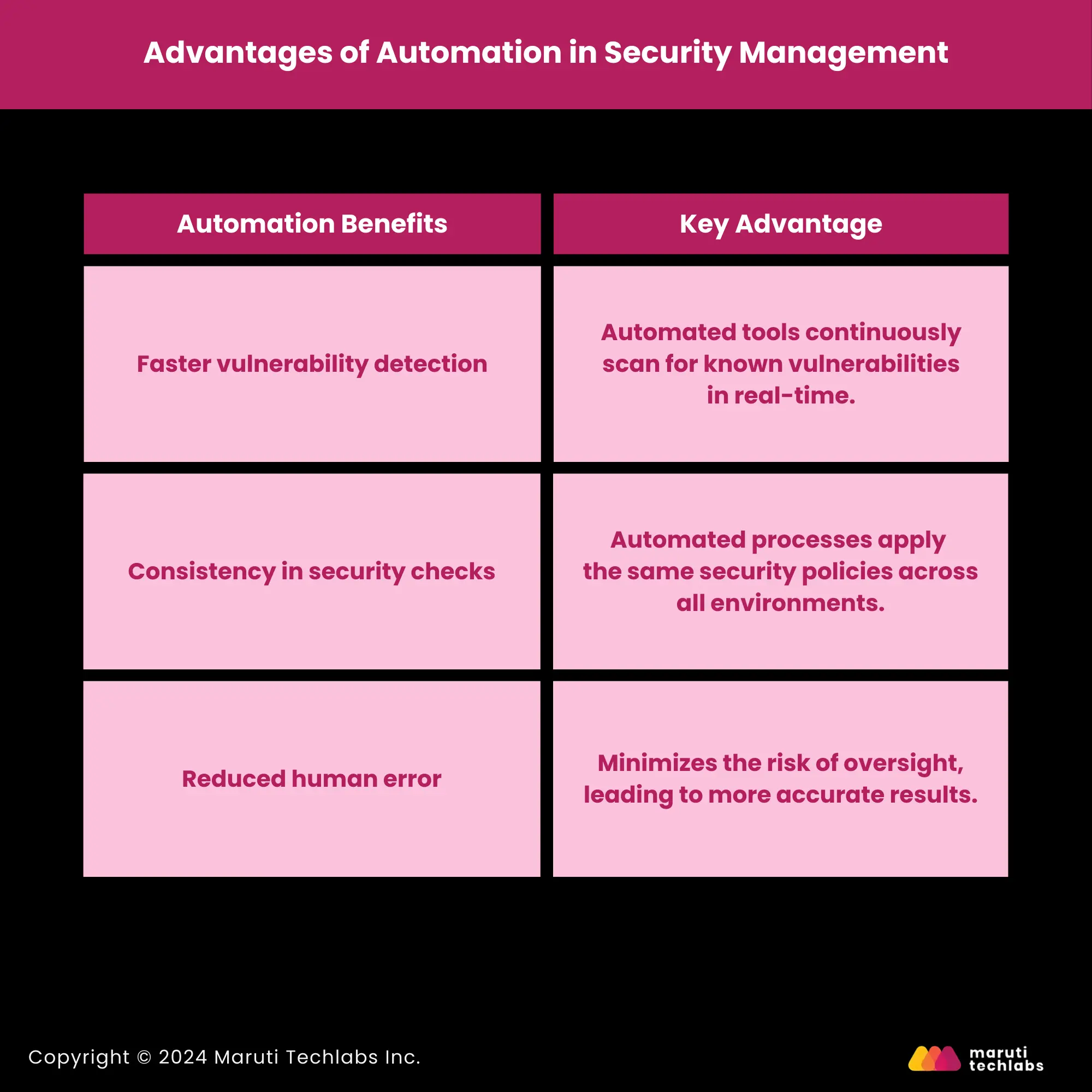
Automation Benefits | Key Advantage |
| Faster vulnerability detection | Automated tools continuously scan for known vulnerabilities in real time. |
| Consistency in security checks | Automated processes apply the same security policies across all environments. |
| Reduced human error | Minimizes the risk of oversight, leading to more accurate results. |
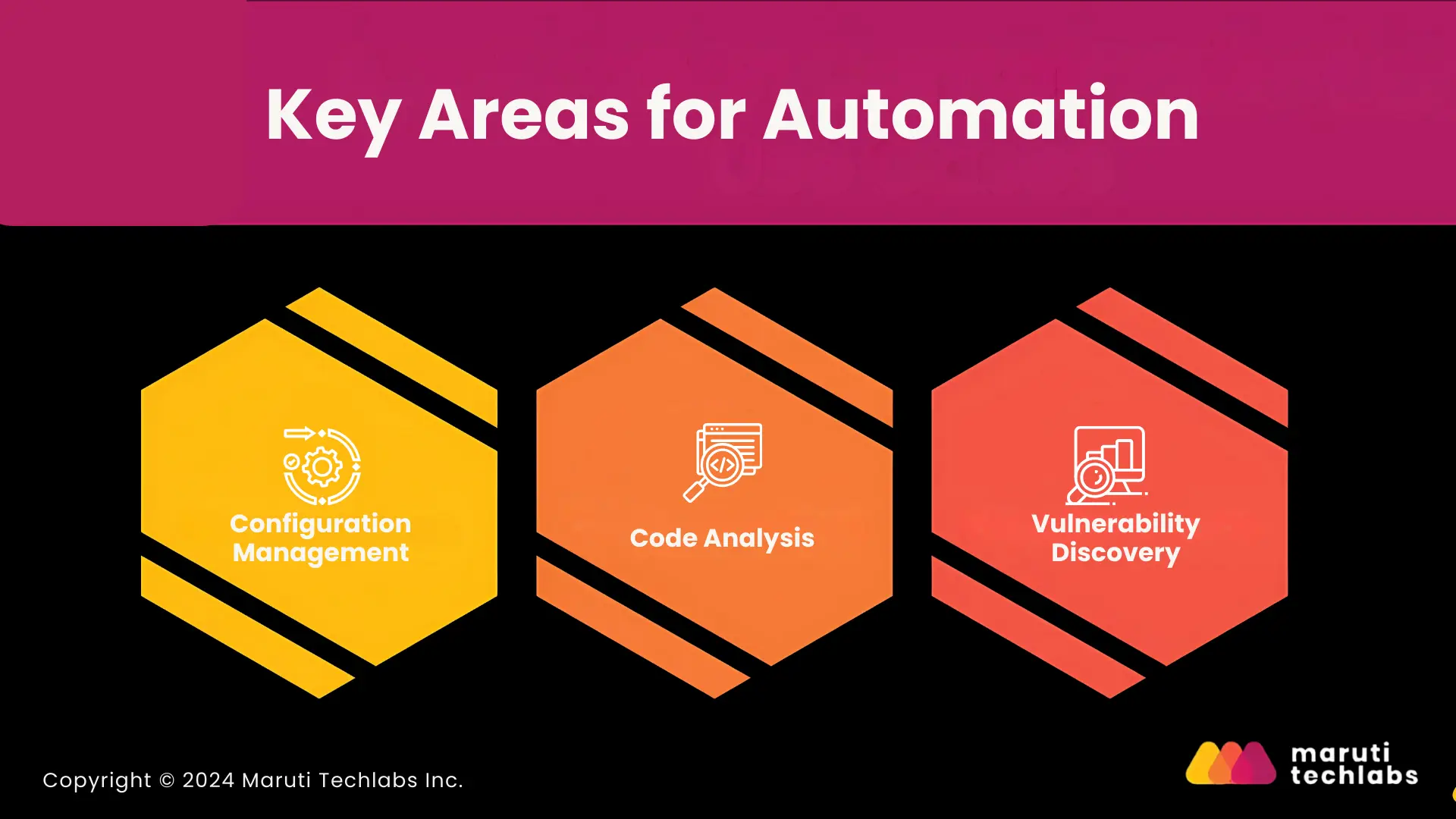
Automating critical tasks can make a significant difference in enhancing security and efficiency. Below are key areas where automation can have the most impact:"
Automation is great, but aligning it with robust governance and policies is equally crucial.
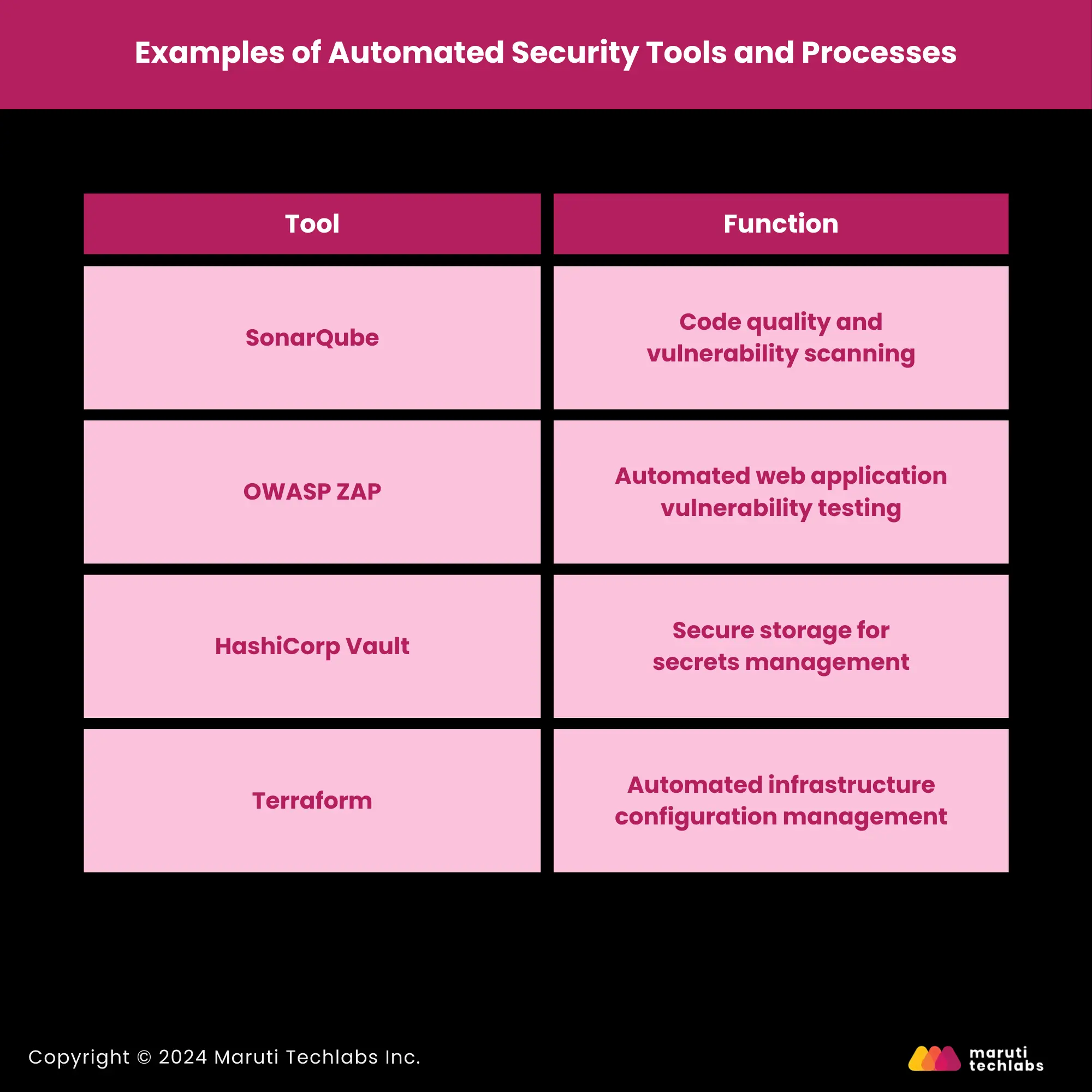
Here are some examples of tools commonly used to automate security processes in DevSecOps environments:
Tool | Function |
| SonarQube | Code quality and vulnerability scanning |
| OWASP ZAP | Automated web application vulnerability testing |
| HashiCorp Vault | Secure storage for secrets management |
| Terraform | Automated infrastructure configuration management |
Maintaining a focused and continuous approach to vulnerability management is essential for staying ahead of evolving threats in today’s dynamic security.
Managing vulnerabilities continuously throughout the development cycle allows teams to proactively address security gaps before they escalate into significant threats, ensuring a more robust defense against attacks.
A key benefit of DevSecOps is the ability to perform continuous vulnerability scanning throughout the development process. Automated tools scan for known vulnerabilities, and development teams can immediately address issues as they arise.
With DevSecOps, vulnerability management should now fall to the development and operations teams. The developers must practice secure coding while the operations team ensures the infrastructure is safe and correctly set up. Sound patch management and updates would only decrease the attack surface.
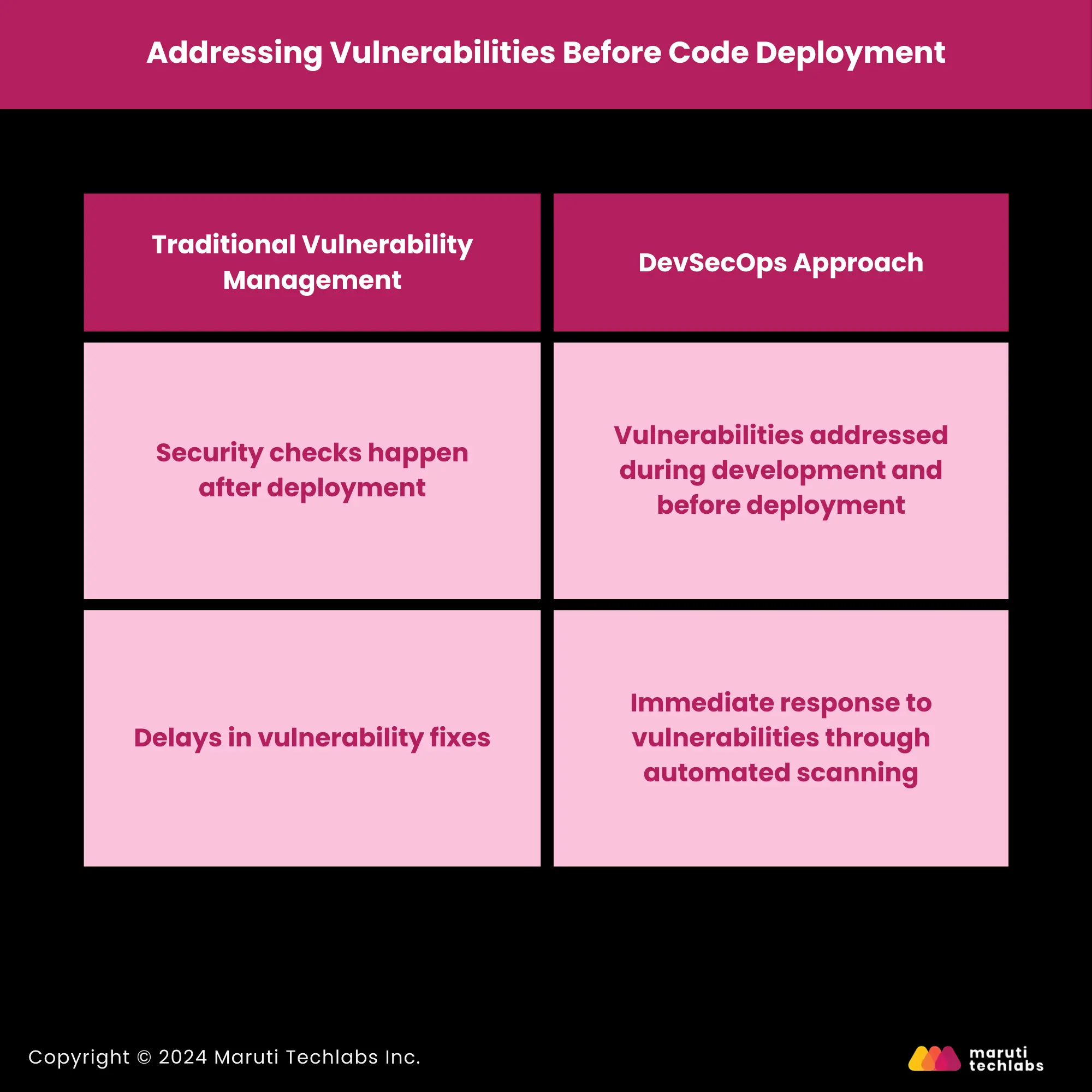
Vulnerabilities must be caught before code deployment to avoid a costly breach. Automated security scans could integrate into the CI pipeline, causing teams to discover vulnerabilities before they become problems.
Traditional Vulnerability Management | DevSecOps Approach |
| Security checks happen after deployment | Vulnerabilities addressed during development and before deployment |
| Delays in vulnerability fixes | Immediate response to vulnerabilities through automated scanning |
Now, let us focus on another vital aspect: secrets and privileged access management.
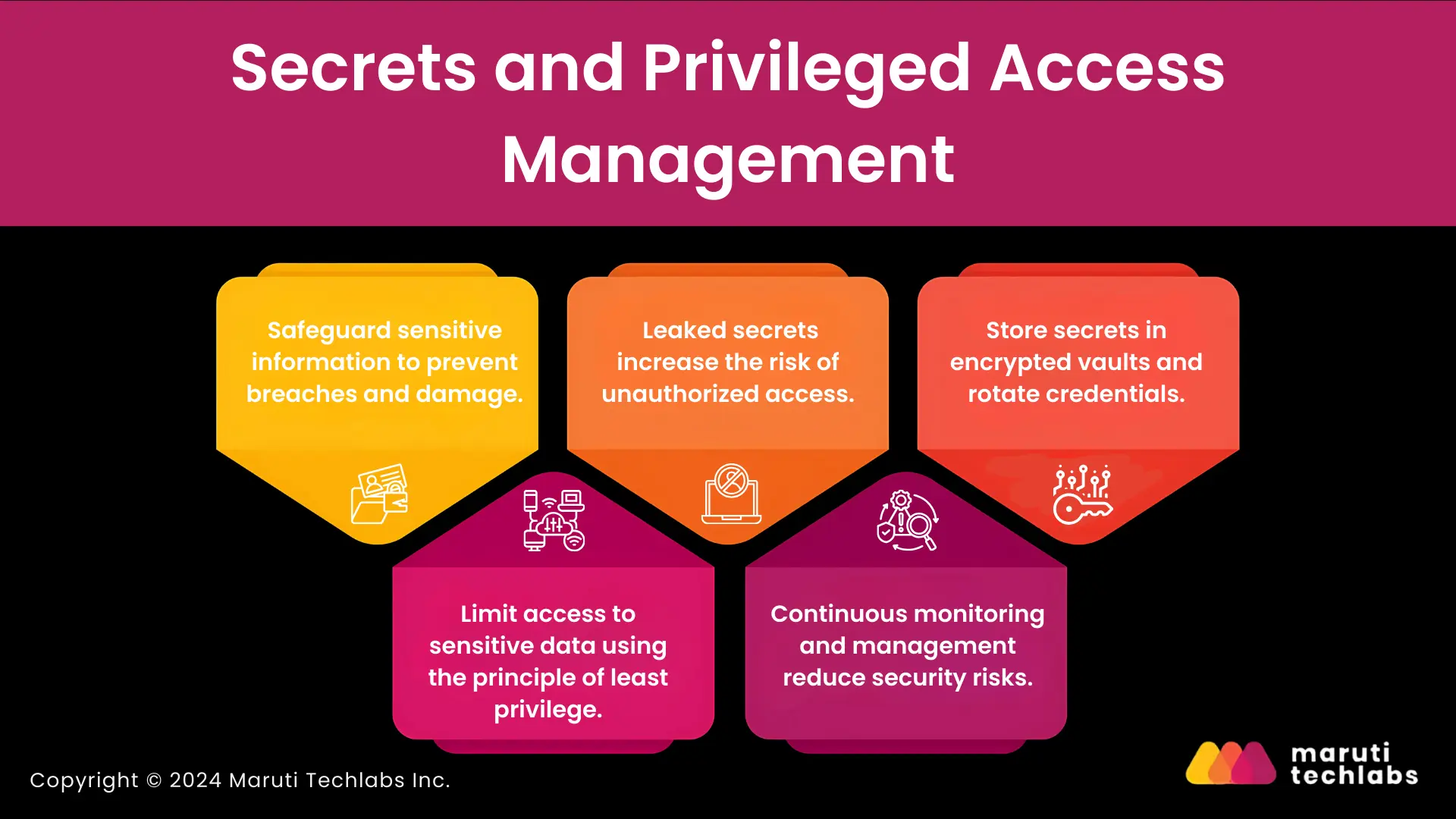
Effective secrets management safeguards sensitive information, reducing the chances of unauthorized access and breaches, which can cause significant financial and reputational damage.
In DevOps, secrets—like API keys, passwords, and tokens—must be securely managed. If not handled properly, secrets can lead to data breaches or unauthorized access. GitGuardian has published a study showing that more than 10 million secrets have been leaked in public GitHub repositories since 2023. This has increased risks as more secrets are not properly managed.
Organizations can improve secrets management by:
The principle of least privilege is fundamental to secure DevOps environments. The risk of data breaches can be reduced by ensuring that users and systems only have the minimum access required to perform their roles.
Focusing on continuous configuration and diligent network management becomes crucial for further reducing risks.
Organizations can prevent common security risks such as misconfigurations and ensure their networks remain secure by continuously monitoring and managing system configurations.
Configuration management is a foundational component of IT security. Misconfigurations—errors in setting up and maintaining system settings—are among the most common sources of security breaches. These errors can expose systems to unauthorized access, data leaks, or other security risks.
Network segmentation is another major practice that enhances security. When an organization divides a network into several segments, it minimizes the exposure of sensitive systems and data. This practice not only promotes security but also introduces the network's overall resilience.
DevSecOps teams can utilize tools such as Ansible, Puppet, or Chef to automate infrastructure configuration. This automation ensures consistency across systems and minimizes the risk of errors caused by manual intervention.
Incorporating security testing into the development process helps in identifying vulnerabilities early and mitigates potential threats before they reach production, significantly reducing the risk of security breaches.
Penetration testing simulates attacks on systems to uncover vulnerabilities that automated tools might miss. Regular automated security scans should complement these tests.
Security testing should be integrated into the development process as part of the CI/CD pipeline. Automated security tests ensure that every code change is tested for vulnerabilities before deployment.
To mitigate threats, organizations should:
Integrating security testing throughout development helps identify vulnerabilities early, reducing risks. A combination of penetration tests, automated scans, and continuous testing within CI/CD ensures robust security. Regular updates, security audits, and incident response procedures are essential for mitigating potential threats.
Security integration into DevOps requires a mindset change in terms of the demand for security at all stages of the SDLC. Through a DevSecOps approach, an organization can produce software as fast as possible without compromising on security.
Key elements for successful DevSecOps implementation include effective vulnerability management, automated deployments, governance, and shared responsibility culture. DevSecOps will be key to ensuring applications and infrastructure security as organizations continue embracing faster development cycles.
Empower your business with cutting-edge technology solutions that prioritize security at every stage. By signing up with Maruti Techlabs, you’ll gain access to expert-driven custom software development, mobile app solutions, and cloud services, all built with a DevSecOps approach to ensure the highest level of security and efficiency.
In today’s fast-paced digital world, businesses face increasing threats and vulnerabilities. Stay ahead of these security challenges with our tailored DevSecOps solutions that streamline operations, protect your software pipeline, and ensure compliance at every step. Contact us today and take the first step toward a secure and innovative future!
DevSecOps integrates security practices into every development stage, ensuring compliance with regulatory standards is built into the software from the outset. Continuous monitoring and automated audits help maintain compliance with regulations such as GDPR and HIPAA, reducing the risk of violations and associated penalties.
Training should focus on secure coding practices, understanding security tools, and threat modeling principles. Additionally, workshops on collaboration between development, operations, and security teams can foster a culture of shared responsibility and improve communication.
In a DevSecOps framework, incident response plans are established as part of the development process. These plans include predefined procedures for detecting, responding to, and recovering from security incidents, ensuring teams can react swiftly and effectively to mitigate damage.
Yes, DevSecOps can be implemented in legacy systems, though it may require additional effort. Organizations can start by integrating security practices into their existing workflows and gradually refactoring legacy code to adopt modern development methodologies while addressing security concerns.
Organizations should track metrics such as the number of vulnerabilities detected and remediated during development, the speed of incident response times, compliance audit results, and the frequency of security training participation. Additionally, monitoring the rate of security-related issues post-deployment can help gauge the effectiveness of the DevSecOps approach.


