

The Ultimate Guide to SOC 2 Audit Logs for Tech Teams in the US






Audit logs capture the intricacies of user interactions, providing traceability. The primary objective behind audit logs includes:
With every action, the system generates a trail of logs and metadata. These records can be used for security, monitoring, cyber forensics, and performance analysis.
These audit logs are a prime necessity when achieving your SOC 2 compliance. SOC 2 stands for Systems and Organizations Controls 2. It helps organizations reduce the risk of security breaches.
Achieving and maintaining SOC 2 compliance means your firm has top-notch security. It offers your clients the confidence and peace of mind they need to do business with you.
This blog covers the importance of audit logs for earning SOC 2 compliance, what makes them developer-friendly, and a checklist that can help you prepare for your SOC 2 compliance certificate.
Security is a top business priority for operating online globally. Audit logs and SOC 2 frameworks help enhance your application or system security. Let’s understand them briefly.
Audit logs, also known as Audit Trails, are a complete and chronological record of all the user actions and system responses captured when using a tech product or service.
They capture details like:
SOC 2 is a security framework that offers a rulebook to help organizations shield their customers’ confidential information against security breaches, unauthorized access, and other vulnerabilities.
SOC 2 was built by the American Institute of Certified Public Accountants (AICPA) around five primary security criteria: availability, processing integrity, security, privacy, and confidentiality.
Audit logs are critical for SOC 2 compliance. They offer crucial evidence to assess an organization’s adherence to the Trust Services Criteria (TSC) required by auditors.
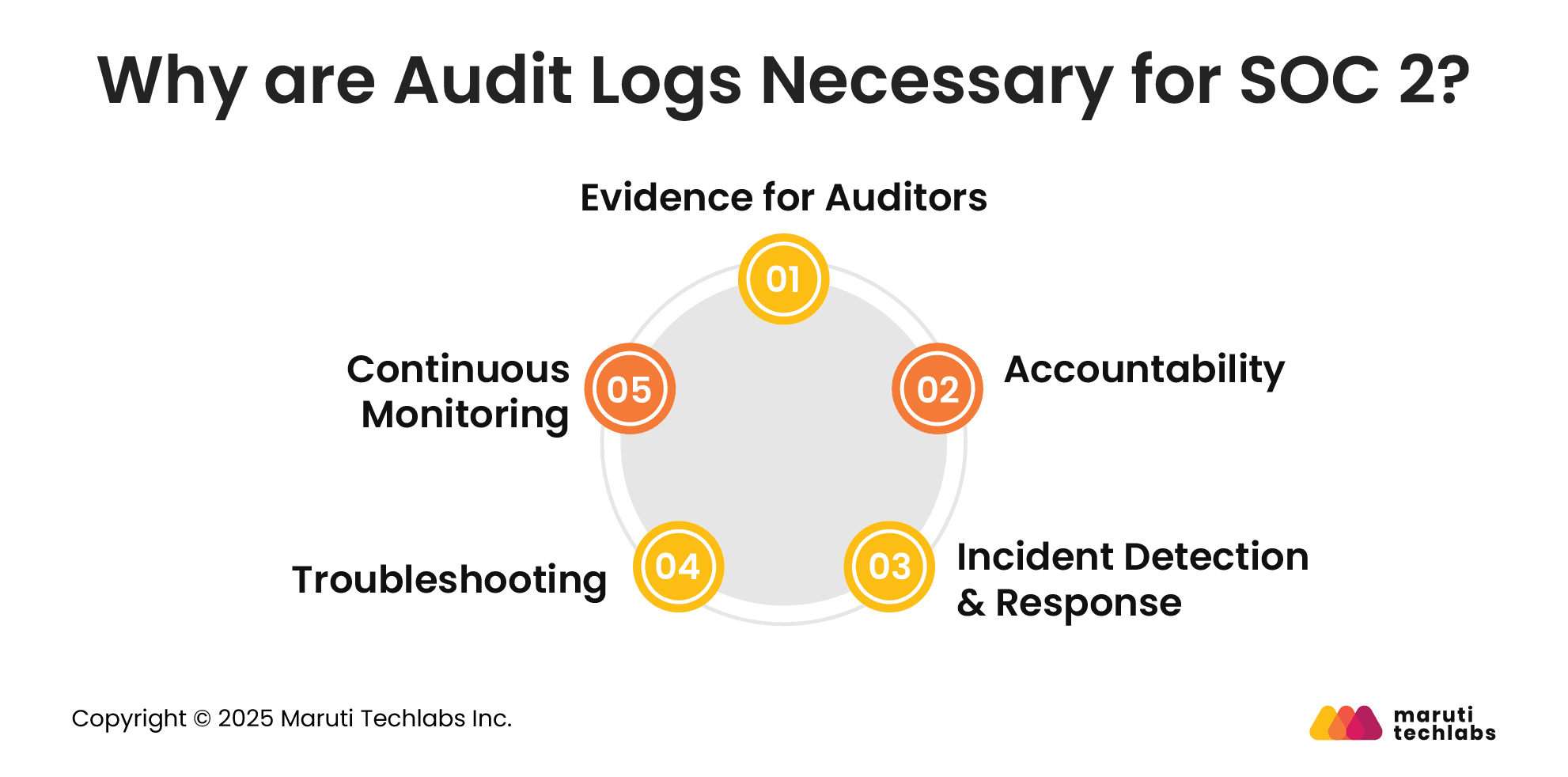
Here’s how audit logs support the SOC 2 TSC criteria.
SOC 2 Type 2 reports require showcasing the operational effectiveness of security mechanisms for 6-12 months. Audit logs become a source of evidence demonstrating that the controls are in place and working as intended.
Logs offer insights into who did what, when, and where. This becomes a fundamental aspect of security and compliance, displaying accountability for actions within systems.
Having audit logs helps organizations do a retrospective analysis where they can learn about unauthorized access attempts and suspicious activity. This is important for devising a robust incident response plan.
Audit logs offer a chronology of events that can create a timeline to identify a root cause and implement security measures during a security breach.
Audit logging facilitates continual monitoring of security controls that helps with knowing and addressing vulnerabilities or proactive control gaps.
A developer-friendly audit logging system is designed to be easy to implement, maintain, and integrate into applications without becoming a burden. Here are the key traits that make audit logging developer-friendly:
If you use formats like JSON with a consistent structure, log aggregation tools like Fluentd and Elastic can gather logs written directly to your app’s standard output stream. However, this accommodation isn’t always possible if you’re already sharing application logs to stdout.
Grafana and Datadog are best recommended for collecting, browsing, and searching logs. Once you’ve uploaded your audit logs, these apps allow you to search by query, like type or timespan.
Structured logs in formats like JSON enable consistent, machine-readable data that's easy to parse, search, and analyze, making them ideal for automation and debugging in development environments.
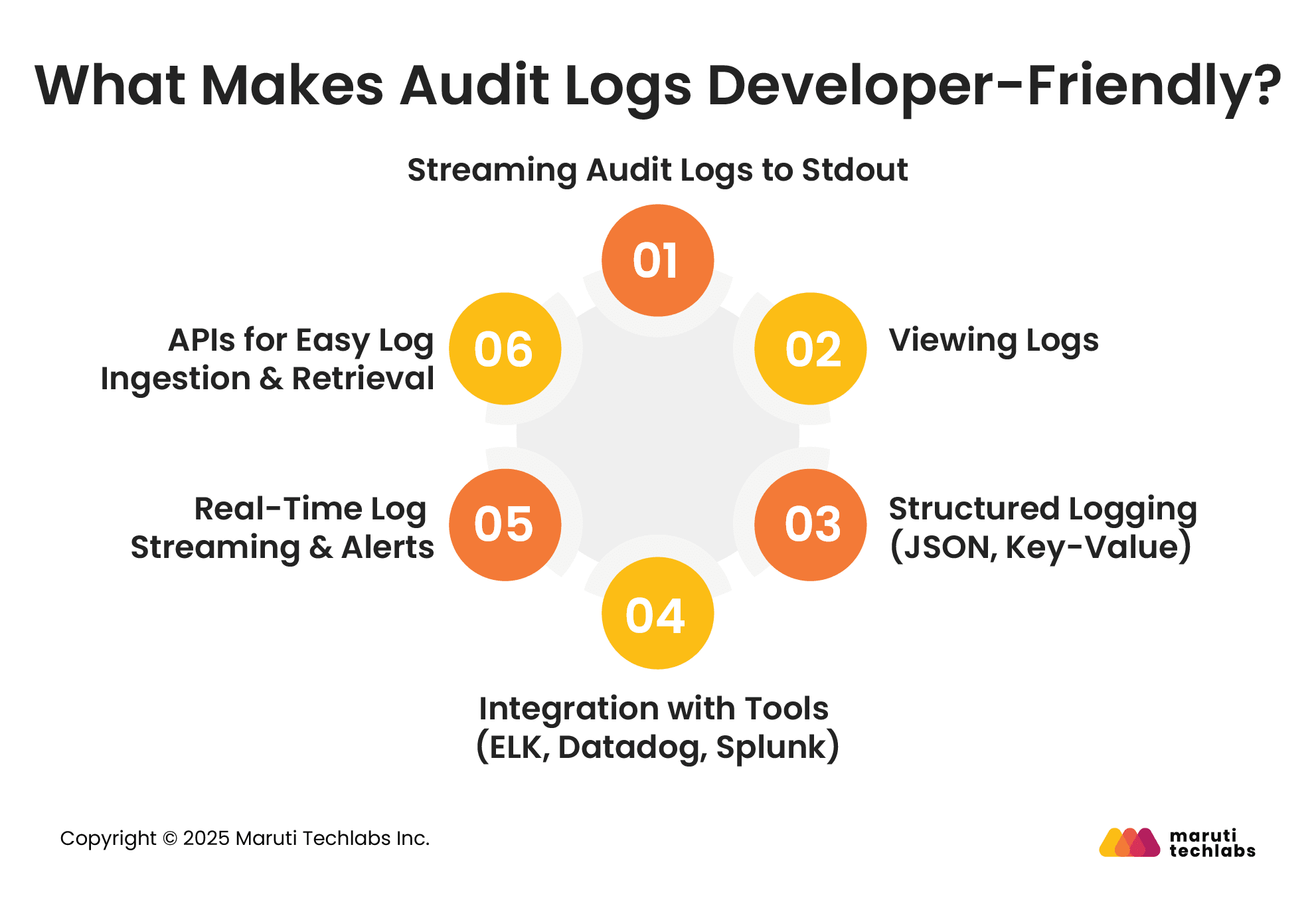
Developer-friendly logging systems offer out-of-the-box compatibility with observability and monitoring tools like ELK, Datadog, and Splunk, streamlining integration and enhancing system visibility.
Support for real-time log streaming and alerting helps developers detect and respond to issues instantly, improving application reliability and accelerating incident response workflows.
Well-documented APIs simplify the process of logging events and retrieving them for analysis, enabling developers to build logging into their applications with minimal friction.
Here is a four-step breakdown that can help you prepare for a SOC 2 audit.
When preparing for an SOC 2 audit, it’s vital to define in-scope systems, such as a SaaS payroll app and tools that document control activities like Jira. It’s suggested that the auditors be consulted early to confirm the scope.
Choose between SOC Type 1, i.e., design-only audit at a point in time, or Type 2, i.e., testing control effectiveness over time. You can also align with frameworks like HIPAA, ISO 27001, HITRUST, NIST CSF, or COBIT.
Generally, a SOC 2 audit requires conducting readiness activities several months in advance. To streamline SOC 2 compliance, hiring an audit firm can offer innumerable benefits. They help businesses discover and rectify gaps, shielding them from potential adverse findings. Aligning with SOC 2 best practices will boost your company’s security and operational effectiveness.
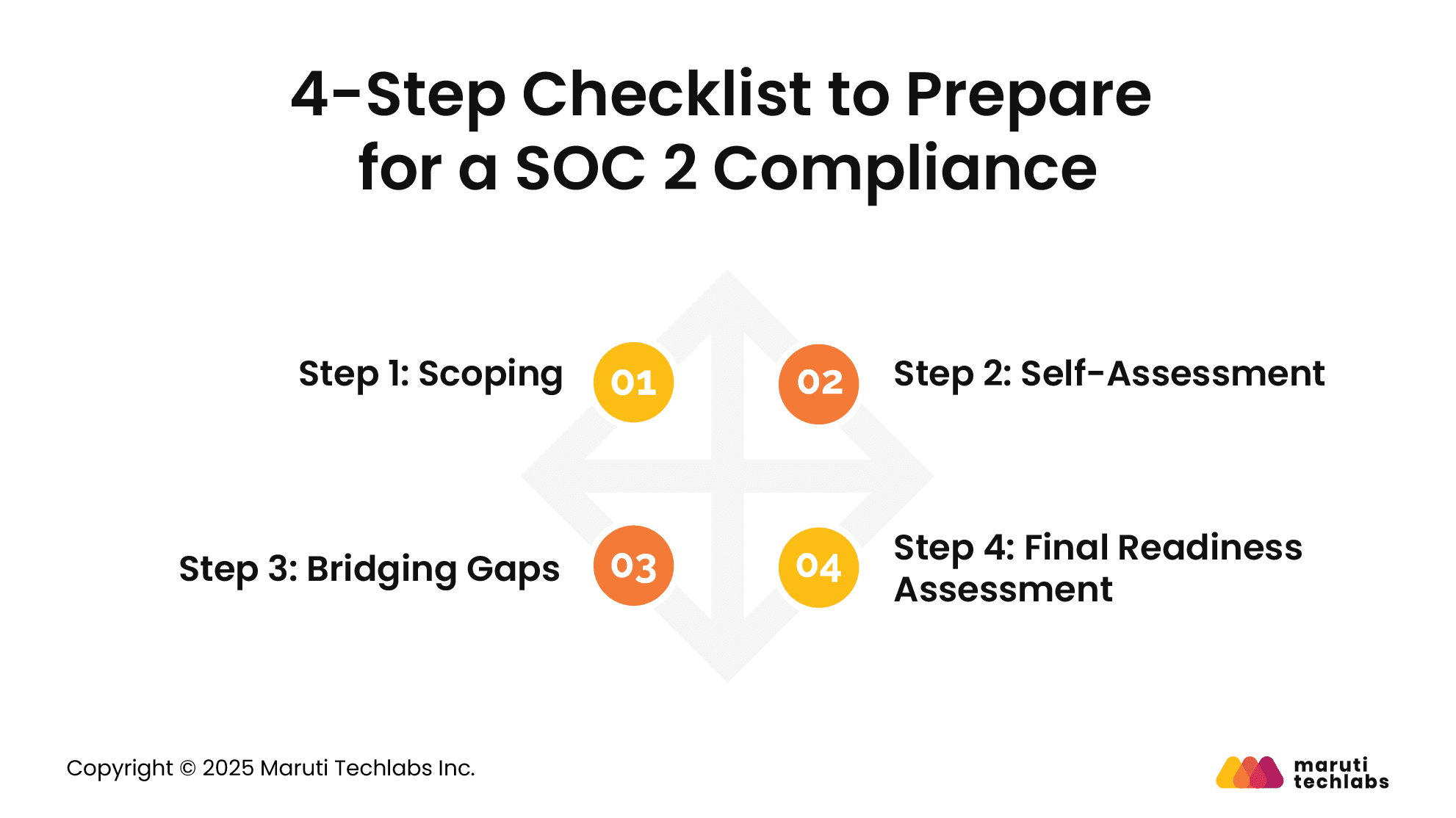
Your self-assessment will help you find gaps that must be addressed and closed before your final SOC 2 audit. The gap remediation process primarily focuses on the following:
A mandatory final readiness assessment reassesses security controls, tests them, and ensures they work as intended. This also re-checks any implementation issues, giving you one final chance to remediate. This will be your last chance to make corrections before partaking in your SOC 2 audit by a third-party CPA firm.
Here are the four crucial reasons that emphasize the importance of SOC 2 compliant audit logs for US businesses.
SOC 2-compliant audit logs help ensure your business complies with major U.S. data privacy regulations, such as CCPA and HIPAA. These regulations demand transparency, access control, and accountability from audit log support.
Logging accounts for traceability of who accessed what data, when, and why. Without this, you risk non-compliance, fines, and reputational damage, especially when handling sensitive customer or patient information.
Large enterprises often require vendors to meet strict compliance standards before signing contracts. SOC 2-compliant audit logs provide concrete evidence that your business monitors access, changes, and security events systematically.
This transparency builds confidence during vendor risk assessments, positioning your company as a trustworthy partner. It proves that you prioritize data integrity and operational accountability—two critical factors in winning enterprise deals and long-term relationships.
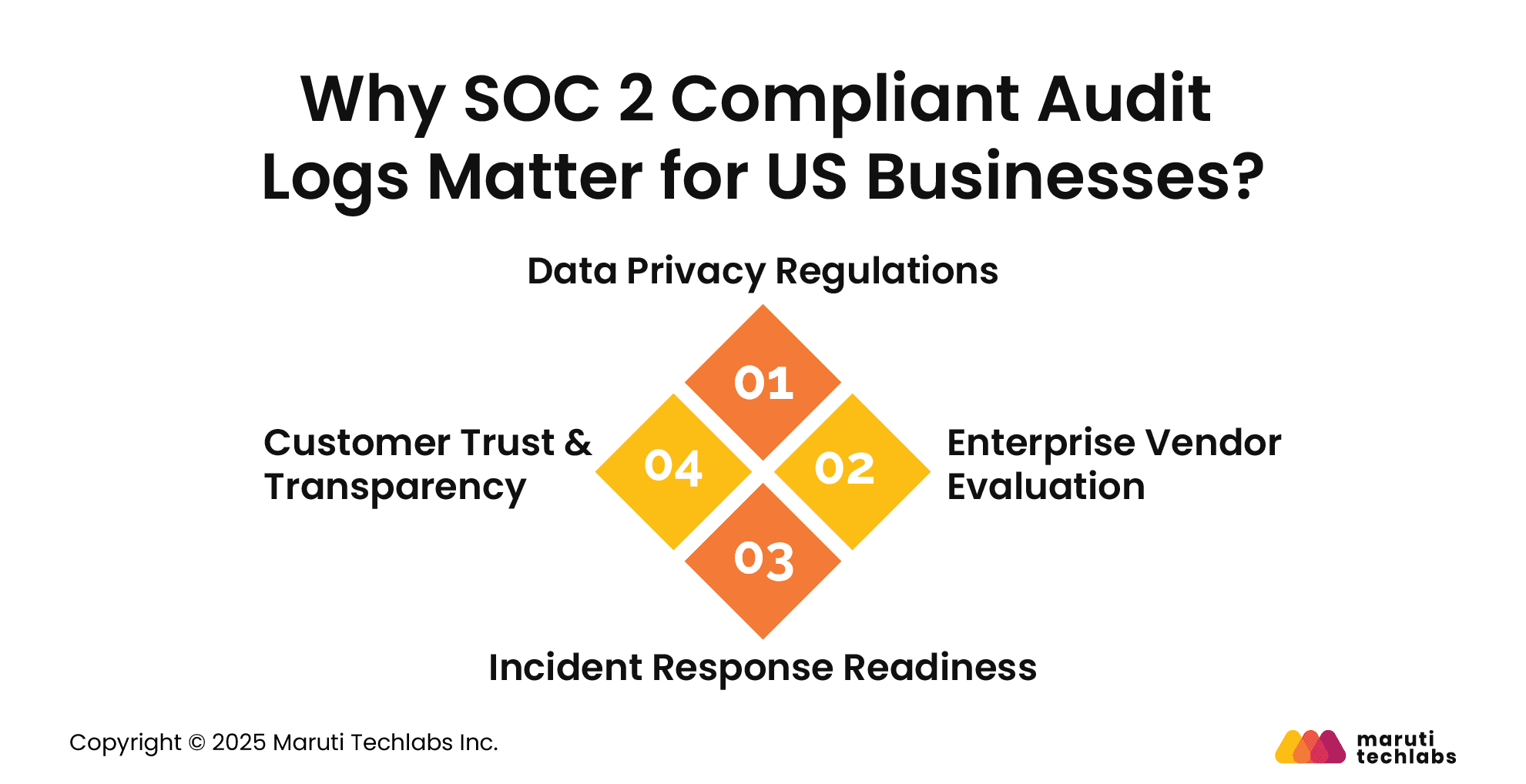
Audit logs are your first line of defense when a security incident occurs. SOC 2-compliant logs ensure detailed, unaltered records of all user activity, essential for root cause analysis and rapid incident resolution.
They also help you prove that your organization took appropriate steps before, during, and after an event. It’s crucial in demonstrating due diligence to regulators, auditors, and stakeholders.
Today’s customers are conscious about how their data is handled. SOC 2 compliant audit logs show your commitment to protecting sensitive information and maintaining operational transparency.
Logging and monitoring all actions is proof that your business values data security. This boosts customer confidence and differentiates your brand in a market where trust is increasingly tied to compliance posture.
Audit logs are a foundational element of SOC 2 readiness. They offer the visibility and accountability needed to demonstrate that your controls work as designed. From access events to system changes, every critical action must be traceable, ensuring your business meets the Trust Services Criteria, mitigates risk, and builds customer trust.
However, compliance shouldn’t compromise developer productivity. The best audit logging systems strike a balance between automating collection and seamlessly integrating with your existing tech stack. Prioritizing developer usability ensures that logging doesn't become a bottleneck but an extension of your engineering workflows.
That’s why it’s essential to invest in the proper logging infrastructure early. A scalable, secure, well-documented system makes audits easier, incidents faster to resolve, and your entire business more resilient.
At Maruti Techlabs, our Technology Advisory Services help you build robust audit logging systems to meet SOC 2 compliance. We also offer enterprise application modernization and code audit services to upgrade and secure your existing software infrastructure.
Don’t wait for a breach or failed audit to realize the importance of your logging foundation. Connect with our experts to learn more about how you can implement audit logging and earn SOC 2 compliance for your business.
If you’re looking for a trusted software development company in Chicago, Maruti Techlabs is here to help you build secure, compliant, and scalable solutions tailored to your business needs.
Audit logs record system activities to ensure accountability, detect security incidents, support forensic investigations, and comply with regulatory requirements. They provide a trail for monitoring and verifying actions.
Audit trails are a detective security control, as they log and monitor activities to identify security incidents or policy violations after they occur.
Audit logs provide an immutable record of user actions, enabling accountability, forensic analysis, and detection of unauthorized access. By documenting who did what and when, they support compliance audits and incident investigations.


