

Cloud Security for GenAI Workloads: Risks, Threat Patterns, and Controls






Generative AI (GenAI) workloads include everything from model training and fine-tuning to real-time inference, automation, and data pipelines that support them. These workloads are now part of everyday business operations and power faster decisions, smoother processes, and better customer experiences. But as GenAI takes on more sensitive tasks, the security stakes rise sharply.
Unlike traditional cloud workloads, GenAI introduces new exposure points: model endpoints, training data flows, and orchestration tools that attackers increasingly target. Attackers today are not just after business data. They are targeting the models, datasets, and logic that power automated decision-making.
With 97% of organizations already struggling with GenAI-related security risks, protecting these systems is no longer optional.
This blog breaks down the key risk patterns, the evolving threat landscape, and a practical SecOps control framework to help you secure GenAI workloads with clarity and confidence.
As reliance on GenAI grows, so do the security risks tied to it. These risks fall into four key categories that organizations must understand to protect their AI systems effectively.
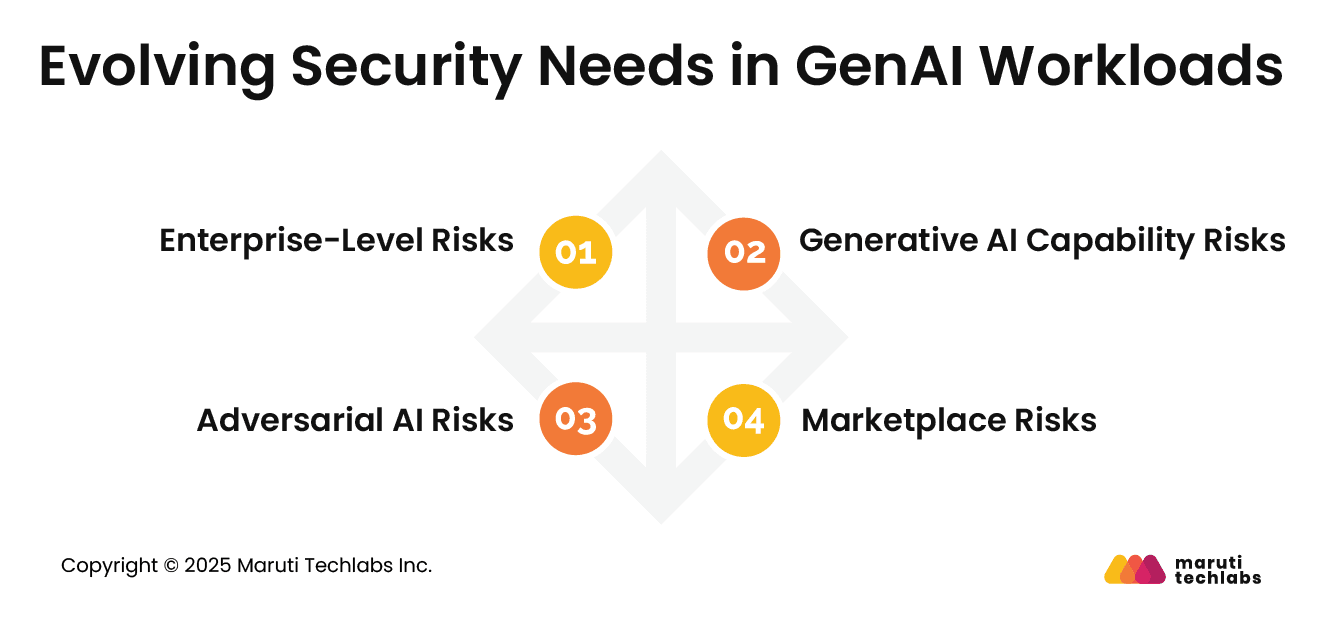
Enterprise risks appear when GenAI interacts with sensitive data, internal tools, or development workflows. Extensive and mixed training datasets can expose private information or intellectual property. Employees also often use GenAI tools without approval, increasing the chances of accidental data leaks or misuse.
These risks focus on weaknesses inside the AI itself. Common issues include prompt injection, data poisoning, evasion attacks, and model hallucinations. When exploited, these gaps can mislead the system, disrupt outputs, or expose hidden information.
Attackers are now using GenAI to enhance cyberattacks. GenAI can help generate more realistic phishing messages, automate malware creation, or produce convincing fake voices and videos. This makes social engineering and impersonation attacks much harder to detect.
Some risks come from the broader ecosystem. Rapid regulatory changes, rising infrastructure demands, hardware shortages, and vendor lock-in can all impact how safely and effectively GenAI is deployed.
Understanding these four risk areas helps security teams build stronger safeguards for GenAI workloads.
AI workloads run across many interconnected systems, creating new risks that attackers are actively exploiting. The issues below are among the most common and damaging in today’s cloud-based AI setups.
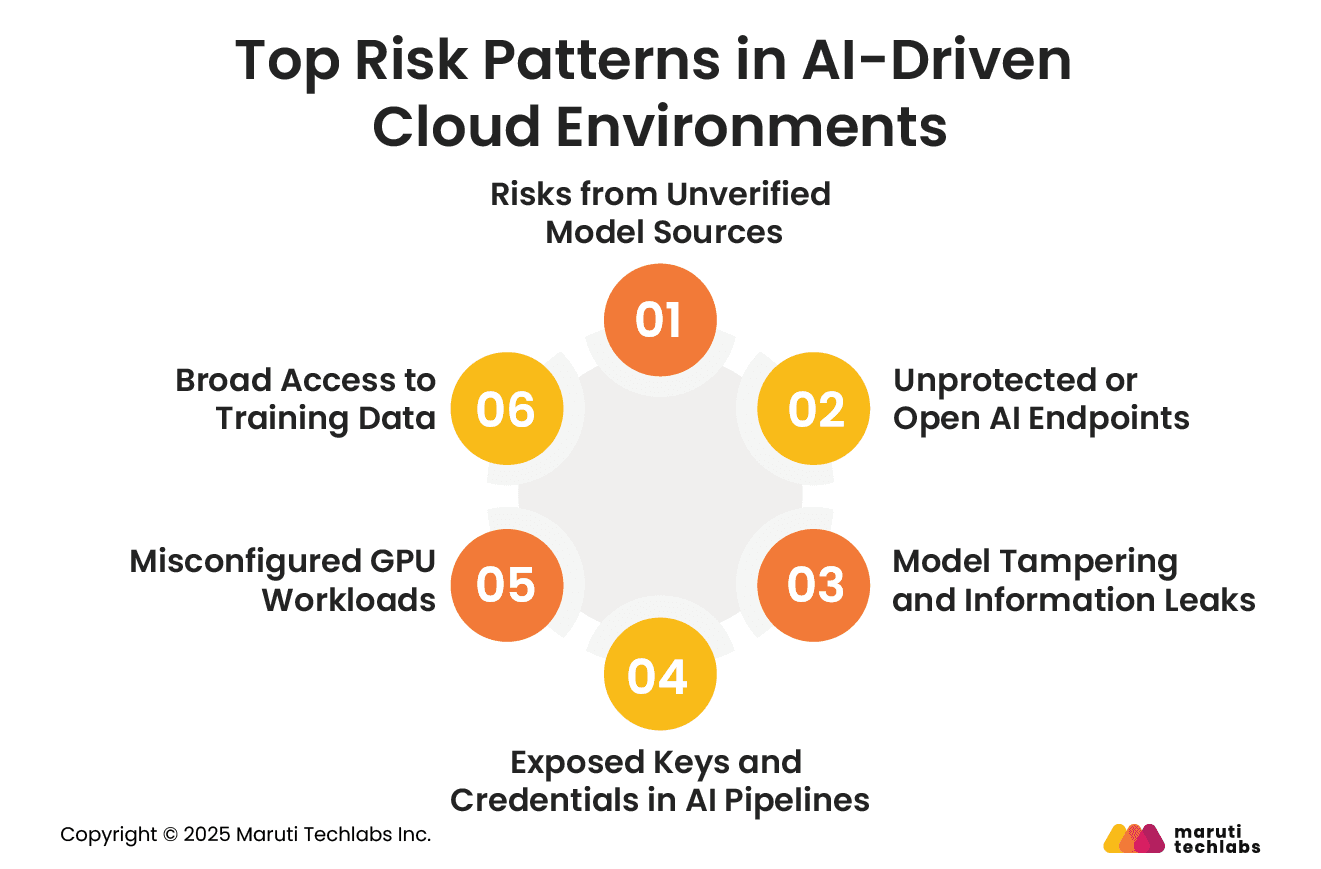
Teams often download ready-made models from public hubs to save time. But if a model has been altered, it may contain hidden code or backdoors. Without proper checks, a single unsafe model can leak data or create an entry point for attackers.
Inference APIs are sometimes deployed quickly and left exposed online. When they aren’t secured, attackers can test prompts, access models, or misuse the API. These endpoints usually sit outside standard monitoring, making unusual activity easy to miss.
Certain prompts can make a model reveal information it was not meant to share. In some cases, attackers can even guess what kind of data the model was trained on, which can expose sensitive patterns or business details.
API keys and tokens often get stored in notebooks, scripts, or CI/CD files. If these files make their way into shared repos, containers, or logs, the credentials leak. One exposed key can allow access to storage, compute, or data pipelines.
GPU-backed environments are powerful and often targeted. If the containers or nodes are not configured correctly, attackers can run unauthorized jobs or disrupt existing workloads, leading to high costs or data risks.
Large training datasets often have wide access permissions to make collaboration easier. But if any token or key is exposed, attackers may reach large volumes of sensitive data, leading to privacy issues or compliance violations.
Cloud SecOps plays a central role in keeping GenAI workloads safe, reliable, and well-governed. As AI systems grow more complex, organizations need security practices that not only protect cloud infrastructure but also understand how AI models, data pipelines, and automation layers behave.
Cloud SecOps helps bring order, clarity, and control to this fast-moving environment.
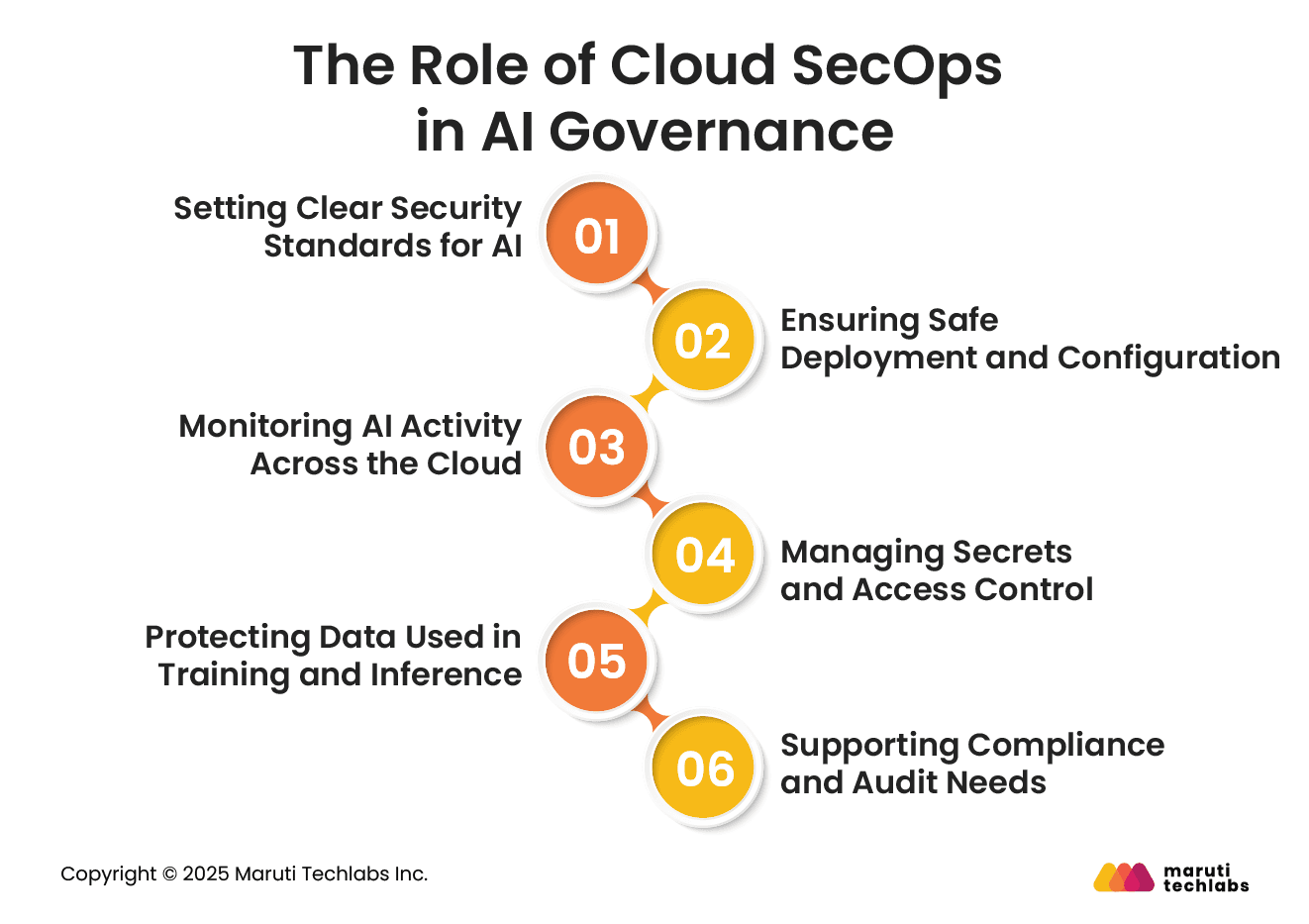
SecOps teams set the basic rules for how AI models and data should be stored, accessed, and monitored. This helps make sure every AI workload is handled safely and follows the same security practices.
AI workloads often involve GPUs, new services, and rapid changes. SecOps helps teams deploy these components safely by checking configurations, permissions, network settings, and resource limits before they go live.
AI systems generate large amounts of traffic and API calls. SecOps provides continuous monitoring to spot unusual behavior early, such as unexpected model access, strange data movements, or sudden spikes in compute use.
AI pipelines rely on many keys, tokens, and service accounts. SecOps keeps these credentials secure, rotates them regularly, and makes sure the right people have the right level of access.
Training and inference often involve sensitive data. SecOps helps control how this data is stored, encrypted, accessed, and logged, reducing the risk of leaks or misuse.
As AI regulations evolve, SecOps ensures that model workflows, data handling, and deployment practices stay compliant. This helps build trust and supports long-term AI governance.
Keeping GenAI workloads safe requires using the right cloud security tools. Each of the tools below focuses on a different part of your cloud setup, helping you reduce risks and stay in control.
CSPM checks your cloud settings and alerts you when something is misconfigured. It helps you spot issues like open storage buckets, weak settings, or missing logs before they turn into real security problems. It’s basically your early warning system for cloud mistakes.
CIEM manages who has access to what in your cloud. It reviews user roles, permissions, and entitlements to make sure no one has more access than they actually need. This reduces the risk of accidental misuse or overly privileged accounts.
CNAPP brings multiple protections together into a single tool. It covers everything from cloud configuration checks to threat detection and workload protection. If you’re building apps directly in the cloud, CNAPP gives you a broad shield across your full environment.
CWPP protects the actual workloads running your AI systems, such as VMs, containers, and serverless functions. It handles tasks such as image scanning, runtime security, and threat monitoring, ensuring workloads remain safe from harmful changes or intrusions.
These tools focus on securing the SaaS apps your teams use every day. They help you control data sharing, check app configurations, and ensure SaaS tools comply with your security standards.
GenAI is bringing huge improvements to how businesses work, but it also introduces new security challenges that can’t be ignored. This blog walks through the major risks, the role of Cloud SecOps, and the tools and practices that help keep AI workloads safe in the cloud.
The main point to remember is that strong security is what keeps GenAI reliable and ready to scale. When your data, models, and cloud systems are protected, your teams can use AI with confidence and avoid unexpected setbacks.
If you’re looking to strengthen the security of your cloud or AI environments, our team at Maruti Techlabs is here to help. You can explore our cloud services page or contact us to learn how we support organizations in building secure, well-governed GenAI systems.
And if cloud modernization or migration is part of your roadmap, our Cloud Migration Cost Calculator can help you estimate costs and plan your security-aligned migration strategy with clarity.
Generative AI workloads introduce risks that traditional cloud systems don’t face. AI models, training data, and inference endpoints become new targets for attackers. These workloads handle sensitive information and often rely on complex pipelines with many moving parts, increasing the risk of misconfiguration.
If not properly secured, models can leak data, be manipulated via prompts, or be stolen. Because GenAI systems learn from data, even small exposures can affect how the model behaves.
Organisations need to watch for threats like tampered AI models from public sources, open or weakly protected inference endpoints, and prompt-based manipulation that reveals sensitive details.
Together, these risks point to where AI ecosystems are most vulnerable.


